Liz Moy
This Machine Ends Data Breaches
#1about 4 minutes
Data breaches are a persistent threat for all companies
Even the largest tech companies suffer from data breaches, highlighting the need for a new approach to security like confidential computing.
#2about 5 minutes
Understanding trusted execution environments (TEEs)
A TEE is a secure, hardware-isolated enclave within a CPU that protects data while it is being processed in memory.
#3about 4 minutes
The three pillars of confidential computing
Confidential computing relies on data confidentiality, data integrity, and remote attestation to provide verifiable security for workloads.
#4about 9 minutes
How remote attestation verifies workload integrity
Attestation is a cryptographic process that proves a TEE has not been tampered with before any sensitive data is sent to it.
#5about 6 minutes
Exploring the confidential computing ecosystem
Major hardware vendors like Intel, AMD, and Nvidia, along with cloud providers, offer a growing ecosystem of TEE-enabled products and services.
#6about 5 minutes
Practical applications and use cases for TEEs
TEEs can be used to process PII, secure credentials, run private ML models, protect IP, and enable multi-party collaboration on sensitive data.
#7about 3 minutes
Demo of a secure medical imaging AI model
This demo shows how to run an ML model for brain tumor detection inside an AWS Nitro Enclave to protect both the model and patient data.
#8about 2 minutes
Demo of a secure financial lending application
A simple mortgage application demonstrates how to isolate and protect sensitive financial calculations within a TEE while integrating with a standard web app.
#9about 7 minutes
The future outlook for confidential computing
While challenges like performance, cost, and side-channel risks exist, the goal is for confidential computing to become a ubiquitous security standard.
#10about 14 minutes
Q&A on implementation, strategy, and AI's impact
The speaker answers audience questions about successful implementations, integrating confidential computing into a security strategy, and the risks of AI in cybersecurity.
Related jobs
Jobs that call for the skills explored in this talk.
Wilken GmbH
Ulm, Germany
Senior
Amazon Web Services (AWS)
Kubernetes
+1
IGEL Technology GmbH
Bremen, Germany
Senior
Java
IT Security
zeb consulting
Frankfurt am Main, Germany
Remote
Junior
Intermediate
Senior
Amazon Web Services (AWS)
Cloud Architecture
+1
Matching moments
05:03 MIN
Understanding confidential computing and trusted execution environments
Safeguarding Sensitive Data Access At Scale with Privacy-Enhancing Technologies

02:16 MIN
How trusted execution environments enable secure collaboration
TikTok's Privacy Innovation

01:47 MIN
Building trusted environments for responsible AI
Bringing AI Everywhere

04:35 MIN
A solution combining serverless and confidential computing
Safeguarding Sensitive Data Access At Scale with Privacy-Enhancing Technologies
01:54 MIN
Learnings and future roadmap for the platform
TikTok's Privacy Innovation

02:41 MIN
Limitations of existing data privacy solutions
TikTok's Privacy Innovation

01:35 MIN
Summary of the data protection architecture
Safeguarding Sensitive Data Access At Scale with Privacy-Enhancing Technologies

05:49 MIN
Cybersecurity is a foundational necessity not a passing trend
Decoding Trends: Strategies for Success in the Evolving Digital Domain
Featured Partners
Related Videos
 29:34
29:34You can’t hack what you can’t see
Reto Kaeser
 37:36
37:36Walking into the era of Supply Chain Risks
Vandana Verma
 40:38
40:38How to Cause (or Prevent) a Massive Data Breach- Secure Coding and IDOR
Anna Bacher
 45:19
45:19Security Challenges of Breaking A Monolith
Reinhard Kugler
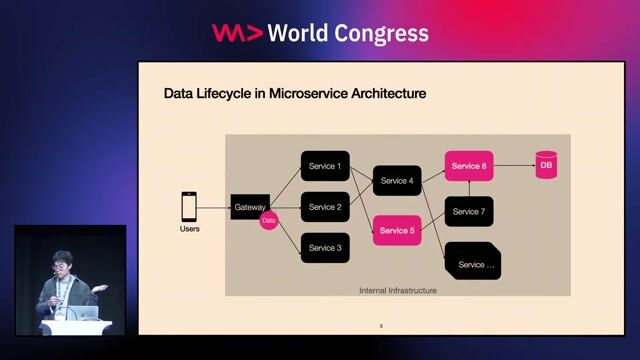 23:52
23:52Safeguarding Sensitive Data Access At Scale with Privacy-Enhancing Technologies
Mingshen Sun
 29:31
29:31Break the Chain: Decentralized solutions for today’s Web2.0 privacy problems
Adam Larter
 20:46
20:46TikTok's Privacy Innovation
Mingshen Sun
 23:50
23:50Data Privacy in LLMs: Challenges and Best Practices
Aditi Godbole
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.

Akamai
Remote
Senior
Azure
Kubernetes
Microservices
Network Security
+2

NTT Data Deutschland SE
Berlin, Germany
Remote
Java
Python
Node.js
Continuous Integration

NTT Data Deutschland SE
Berlin, Germany
Remote
Java
Python
Node.js
Continuous Integration



NTT Data Deutschland SE
München, Germany
Java
DevOps
Python
Node.js
Continuous Integration

Punk Security Ltd.
Remote
£30-40K
Junior
Go
Java
.NET
+9

NEXT DIGITAL
Remote
Terraform
Continuous Integration
Amazon Web Services (AWS)
Scripting (Bash/Python/Go/Ruby)

Devoteam
IIS
Linux
ServiceNow
Google Cloud Platform
Amazon Web Services (AWS)
+1