{"@context":"https://schema.org","@graph":[{"@context":"https://schema.org/","@type":"JobPosting","@id":"#jobPosting","title":"Senior Security Consultant
Role details
Job location
Tech stack
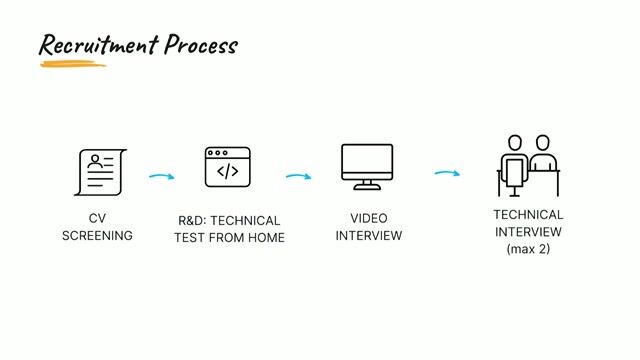
Job description
- Conduct penetration tests (network, social, physical, adjacent, and more) that target Organizations, Networks, Application and Cloud infrastructure and evaluate their security defenses in depth.
- Assess the security posture of applications (mobile, web / cloud, core networks, etc.) via functional testing, fuzz testing and other applicable methodologies.
- Review the security maturity of edge systems (IoT, kiosk terminals, operator terminals, etc.) that are interconnected via public or private networks.
- Conduct targeted research to understand vendor-specific technology, identify its security-critical components, and prioritize impactful attack vectors.
- Document and present security risks & mitigation recommendations in both technical- and business-oriented language.
Requirements
-
BSc or MSc in Electrical Engineering, Computer Science, Computer Engineering, or equivalent practical experience.
-
4+ years of experience in VAPT, IT security or application security (mobile, web front-end, backend, etc.) related roles.
-
Proven experience in vulnerability assessment, penetration testing or security testing at the network, application, or system level.
-
Active Directory and Cloud Infrastructure Knowledge. Key Skills
-
Experience with Information Security fundamentals (risk management, security best practices, data protection, communication encryption, authentication, authorization, etc.) and cyber threats of modern systems & networks.
-
Experience with the technologies and security controls present in application (web full-stack, WAF, EDR, data encryption, transport protection, etc.), network (firewalls, segmentation, IDS / IPS, VPN, etc.) and Windows / Linux system (privileges, roles / groups, AV / Endpoints, secret storage, etc.) architectures.
-
Experience identifying, exploiting, and reporting vulnerabilities in the context of Red Team / VAPT tasks (OWASP Web / Mobile Top10 vulnerabilities, access control, insecure configurations, secrets management, etc.).
-
Experience with Active Directory attacks (Pass-the-Hash, Pass-the-Ticket, Kerberoasting, Golden Ticket, Silver Ticket, DCSync, Credential dumping, Abuse of ACLs, Lateral movement via SMB, etc.).
-
Experience using pentest and other security related tools for information gathering, vulnerability discovery, exploitation, evasion, persistence, and pivoting in Cloud environments.
-
Experience with authentication, authorization, role-based ACL, identity, and access management methods, such as OAuth, MFA, SSO, JWT, PKI, Cloud IAM, etc.
-
Experience with basic cryptographic primitives, such as symmetric & asymmetric encryption, authenticated encryption, key derivation, and key exchange.
-
Ability to monitor the current threat landscape, emerging threads and follow their technical analysis & published exploitation techniques.
-
Problem-solving skills, analytical thinking, and willingness to learn / grow.
-
Proficient in English and excellent communication skills.
Benefits & conditions
- Act with Integrity - We uphold the highest ethical standards and take full responsibility in every action.
- Collaborate with Trust - We bring together diverse perspectives across disciplines and borders.
- Challenge with Curiosity - We question deeply, explore fearlessly, and pursue knowledge relentlessly.
- Innovate to Protect - We create with purpose, building secure, scalable, and forward-looking solutions.
- Adapt with Precision - We move with speed and discipline - learning from failure and refining our approach. Ready to Make an Impact? Apply today! #J-18808-Ljbffr