Jasmin Azemović
Security Pitfalls for Software Engineers
#1about 4 minutes
The high cost and consequences of security breaches
Major companies like Uber and Microsoft have suffered massive data breaches, costing millions and highlighting the severe financial and reputational risks of poor security.
#2about 6 minutes
Foundational practices for writing secure software code
Writing secure code starts with fundamental practices like proper input validation, applying threat modeling methodologies like STRIDE, and adhering to the principle of least privilege.
#3about 5 minutes
Mitigating supply chain attacks with DevSecOps practices
Vulnerabilities in third-party libraries, like the SolarWinds and Log4j incidents, necessitate a DevSecOps approach to integrate security checks throughout the software development lifecycle.
#4about 2 minutes
Essential security measures for protecting public APIs
Publicly exposed APIs must be protected using strong authentication, TLS/SSL encryption for data in transit, and defenses against common attack vectors.
#5about 5 minutes
Protecting data with database encryption and temporal tables
Encrypting sensitive data at the database level protects it even if breached, while temporal tables provide a complete audit trail for forensic analysis.
#6about 2 minutes
Implementing a robust penetration testing strategy
Regular penetration testing, distinct from QA, should be a standard practice using methodologies like black-box or white-box testing and frameworks like the OWASP Top 10.
#7about 1 minute
Maintaining security by separating work and personal devices
Avoid using company-issued laptops for personal or freelance projects to prevent legal liabilities and security compromises between environments.
#8about 3 minutes
Q&A on vulnerable libraries and team security responsibility
The session concludes with answers to audience questions about tracking open-source vulnerabilities, choosing a pen test environment, and clarifying security roles within an agile team.
Related jobs
Jobs that call for the skills explored in this talk.
Architekt für Cloud Security - AWS (w|m|d)

zeb consulting
Frankfurt am Main, Germany
Remote
Junior
Intermediate
Senior
Matching moments

01:58 MIN
Cybersecurity is a foundational necessity not a passing trend
Decoding Trends: Strategies for Success in the Evolving Digital Domain

00:28 MIN
Why developers make basic cybersecurity mistakes
Don't Be A Naive Developer: How To Avoid Basic Cybersecurity Mistakes

24:17 MIN
Shifting security left with collaborative threat modeling
We adopted DevOps and are Cloud-native, Now What?
28:05 MIN
A developer's responsibility to build secure software
You can’t hack what you can’t see
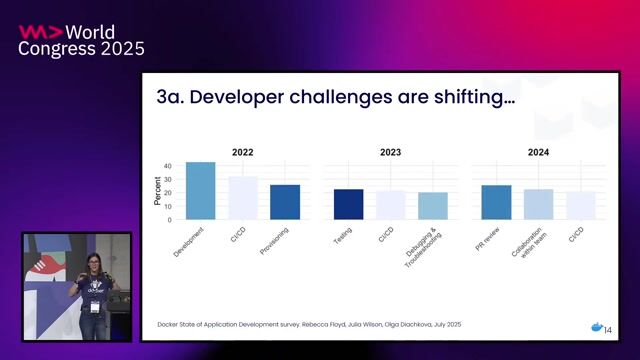
14:01 MIN
Security is now a shared responsibility across all teams
The Evolving Landscape of Application Development: Insights from Three Years of Research
27:19 MIN
Key takeaways on IDE and developer tool security
You click, you lose: a practical look at VSCode's security

15:35 MIN
Modern cybersecurity challenges for developers
Cyber Security: Small, and Large!
02:55 MIN
Why security is often neglected in development
Security in modern Web Applications - OWASP to the rescue!
Featured Partners
Related Videos
 1:58:48
1:58:48Software Security 101: Secure Coding Basics
Thomas Konrad
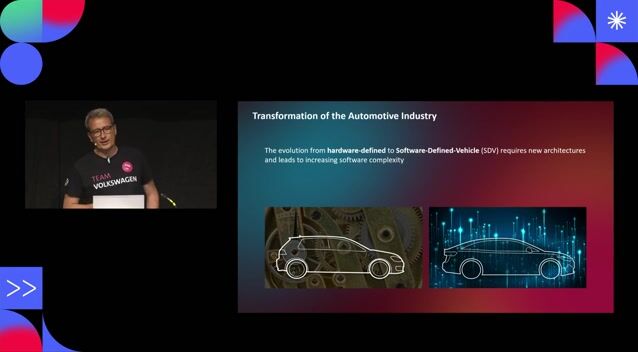 22:09
22:09Cybersecurity for Software Defined Vehicles
Henning Harbs
 29:34
29:34You can’t hack what you can’t see
Reto Kaeser
 29:47
29:47You click, you lose: a practical look at VSCode's security
Thomas Chauchefoin & Paul Gerste
 48:02
48:02Building Security Champions
Tanya Janca
 51:41
51:41Climate vs. Weather: How Do We Sustainably Make Software More Secure?
Panel Discussion
 44:30
44:30Securing Your Web Application Pipeline From Intruders
Milecia McGregor
 37:32
37:32Cyber Security: Small, and Large!
Martin Schmiedecker
From learning to earning
Jobs that call for the skills explored in this talk.


IT-Security Engineer Awarness Training and Security Roadmap
Paris Lodron-Universität Salzburg
Powershell
Windows Server
Microsoft Office
Scripting (Bash/Python/Go/Ruby)




Cybermenaces des produits, quelles activités et stratégies adopter pour permettre au product security officer d'y faire face?
Wavestone
Canton of Courbevoie-2, France


Cybermenaces des produits, quelles activités et stratégies adopter pour permettre au product security officer d'y faire face?
Wavestone
Canton of Courbevoie-2, France








Backend Software Engineer AI - Cybersecurity
Client Server
Esher, United Kingdom
Remote
€95-130K
Go
C++
Java
+1


Cyber Security Content Engineer, Blue Team - Azure
TryHackMe
Charing Cross, United Kingdom
Remote
€46K
Intermediate
PHP
Bash
Azure
+2

