Jon Geater
Overcome your trust issues! In a world of fake data, Data Provenance FTW
#1about 6 minutes
Understanding the risks of the modern software supply chain
Vulnerabilities in common dependencies like Log4j demonstrate how the entire software ecosystem is at risk from a single point of failure.
#2about 12 minutes
Moving beyond software to address the data supply chain
The problem of trust extends from code to data, where AI-generated images and fraudulent documents pose significant business risks.
#3about 4 minutes
The failure of traditional perimeter-based security models
Despite record spending on cybersecurity, high-profile breaches like stolen signing keys show that traditional security approaches are no longer sufficient.
#4about 4 minutes
Introducing a new trust model based on data provenance
A shift to a "verify then trust" model using data provenance provides a more robust way to ensure integrity in a highly connected world.
#5about 4 minutes
Core principles of the IETF standard for integrity
The SCITT standard establishes trust through three key principles: strong identification, immutability, and transparency to prevent equivocation.
#6about 4 minutes
Implementing data provenance with APIs and distributed ledgers
An open source API uses distributed ledger technology to create verifiable, offline receipts for any data attestation, from IoT to SBOMs.
#7about 9 minutes
A live demonstration of creating a verifiable data claim
A simple API call attests a piece of data, creating an immutable and publicly verifiable record on a distributed ledger.
Related jobs
Jobs that call for the skills explored in this talk.
ROSEN Technology and Research Center GmbH
Osnabrück, Germany
Senior
TypeScript
React
+3
VECTOR Informatik
Stuttgart, Germany
Senior
Kubernetes
Terraform
+1
Matching moments

06:13 MIN
Understanding the synergy of AI and blockchain technology
Exploring 5 Key Applications of AI Abundance with Blockchain Assurance

02:35 MIN
Using blockchain for data traceability and transparency
How to Build for Decentralized Systems
02:25 MIN
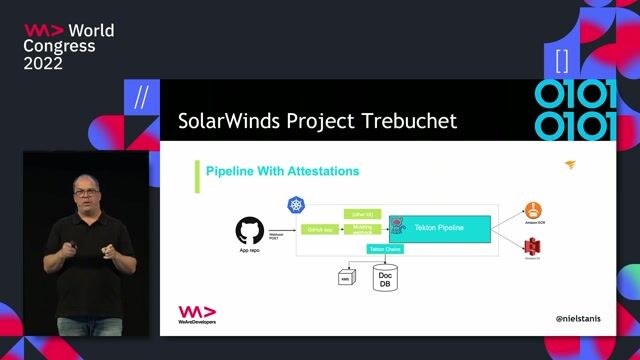
Implementing and enforcing supply chain policies
Securing your application software supply-chain
01:46 MIN
Building trust through transparent data privacy
IKEA Story: Transforming an Iconic Retail Brand
01:31 MIN
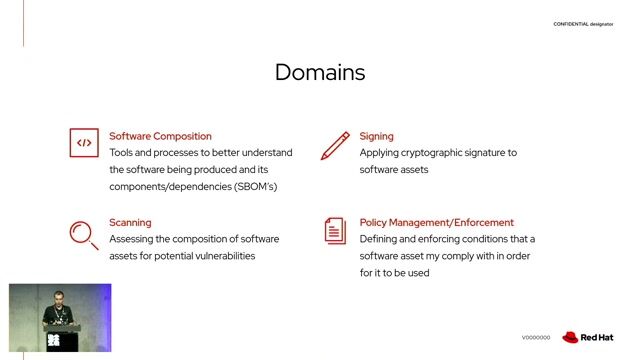
Exploring the core domains of supply chain security
Open Source Secure Software Supply Chain in action
09:15 MIN
Q&A on blockchain, pentesting, and ethical implications
Reverse Vending Machine (RVM) Security: Real World Exploits / Vulnerabilities

03:14 MIN
Implementing best practices for trustworthy AI systems
Data Privacy in LLMs: Challenges and Best Practices

01:50 MIN
Ensuring content authenticity in the AI era
Fireside Chat with Cloudflare's Chief Strategy Officer, Stephanie Cohen (with Mike Butcher MBE)
Featured Partners
Related Videos
 28:27
28:27Securing your application software supply-chain
Niels Tanis
 32:55
32:55Open Source Secure Software Supply Chain in action
Natale Vinto
 41:06
41:06From Monolith Tinkering to Modern Software Development
Lars Gentsch
 29:31
29:31Break the Chain: Decentralized solutions for today’s Web2.0 privacy problems
Adam Larter
 30:40
30:40The Clean as You Code Imperative
Olivier Gaudin
 24:33
24:33GenAI Security: Navigating the Unseen Iceberg
Maish Saidel-Keesing
 28:14
28:14Exploring 5 Key Applications of AI Abundance with Blockchain Assurance
ED MARQUEZ
 24:47
24:47Supply Chain Security and the Real World: Lessons From Incidents
Adrian Mouat
Related Articles
View all articles


.gif?w=240&auto=compress,format)
From learning to earning
Jobs that call for the skills explored in this talk.


DoiT
Amsterdam, Netherlands
Remote
Intermediate
Go
Java
Azure
Spark
+9


Trinamics
Utrecht, Netherlands
€3-6K
C++
Machine Learning

Government Digital & Data
Manchester, United Kingdom

TRUSTEQ GmbH
München, Germany



Provectus
Remote
Intermediate
API
ETL
Azure
Scrum
+10