Niels Tanis
Securing your application software supply-chain
#1about 3 minutes
Defining the modern software supply chain
The modern software supply chain encompasses all steps from source code to deployment, growing in complexity with cloud-native development.
#2about 1 minute
Learning from the SolarWinds supply chain attack
The SolarWinds incident serves as a key example of a supply chain attack where a compromised build server injected malicious code into a signed product.
#3about 3 minutes
Securing developer access and development tools
Protect source code access by implementing multi-factor authentication and git commit signing, while also considering the security risks within your IDE's own supply chain.
#4about 5 minutes
Managing risks from third-party libraries
Mitigate risks from third-party dependencies by addressing vulnerabilities, preventing dependency confusion, and using tools like OpenSSF Security Scorecards to assess package health.
#5about 3 minutes
Ensuring integrity with reproducible builds and signing
Create verifiable software by implementing reproducible builds and using tools like Sigstore and Cosine for keyless signing of artifacts like Docker images.
#6about 4 minutes
Creating a software bill of materials (SBOM)
A Software Bill of Materials (SBOM) acts like a parts list for your software, enabling you to track all components using tools like CycloneDX and Syft.
#7about 3 minutes
Adopting the SLSA framework for supply chain maturity
The SLSA framework provides a maturity model with incremental levels to help organizations progressively secure their software supply chain.
#8about 2 minutes
Implementing and enforcing supply chain policies
Apply supply chain security in practice with validation pipelines like SolarWinds' Project Trebuchet and enforce policies using tools like Kyverno and Google's Binary Authorization.
#9about 3 minutes
Key takeaways and next steps for securing your supply chain
The key to securing your supply chain is to be aware of its complexity, integrate security from the start, and begin by generating and eventually ingesting SBOM data.
Related jobs
Jobs that call for the skills explored in this talk.
ROSEN Technology and Research Center GmbH
Osnabrück, Germany
Senior
TypeScript
React
+3
VECTOR Informatik
Stuttgart, Germany
Senior
Kubernetes
Terraform
+1
IGEL Technology GmbH
Bremen, Germany
Senior
Java
IT Security
Matching moments
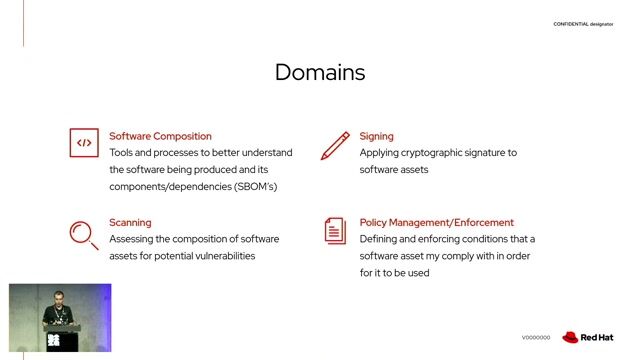
01:31 MIN
Exploring the core domains of supply chain security
Open Source Secure Software Supply Chain in action
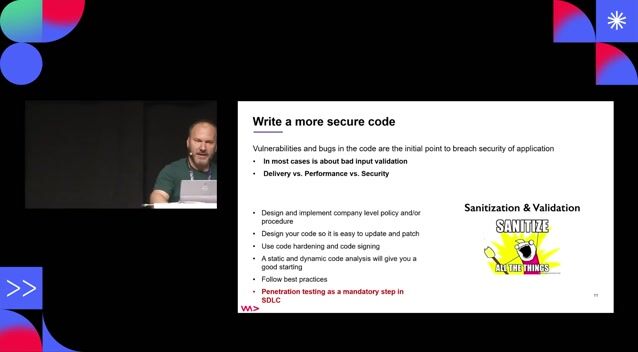
04:45 MIN
Mitigating supply chain attacks with DevSecOps practices
Security Pitfalls for Software Engineers

01:46 MIN
Understanding the rising threat to software supply chains
Open Source Secure Software Supply Chain in action
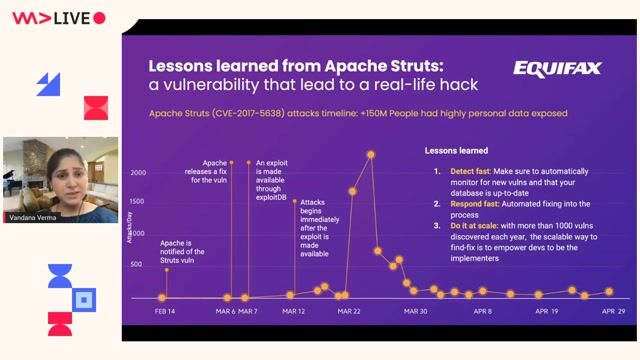
03:32 MIN
Defining the modern software supply chain
Walking into the era of Supply Chain Risks
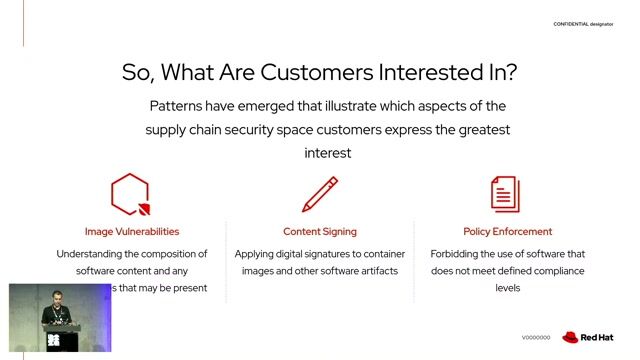
02:21 MIN
Defining key standards and terminology in supply chain security
Open Source Secure Software Supply Chain in action
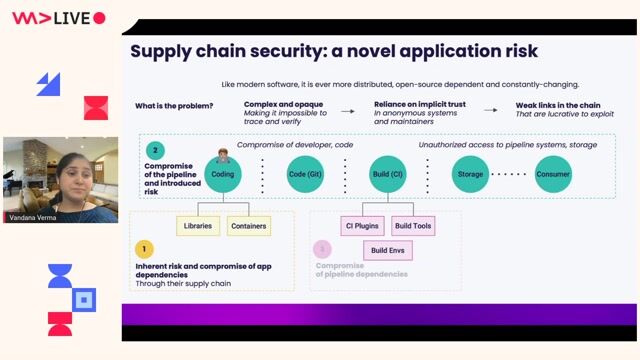
03:50 MIN
Building a foundation for pipeline security
Walking into the era of Supply Chain Risks
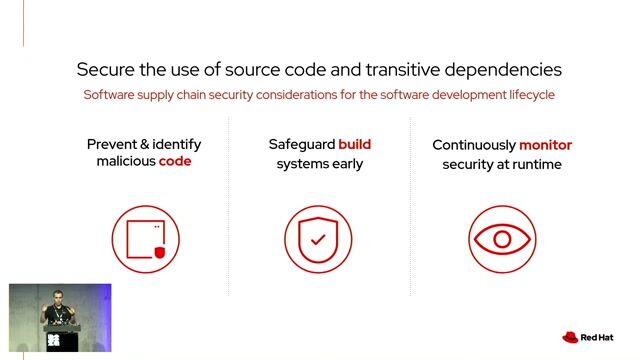
04:51 MIN
Using open source tools to secure the entire SDLC
Open Source Secure Software Supply Chain in action

04:40 MIN
Integrating security throughout the CI/CD process
Plan CI/CD on the Enterprise level!
Featured Partners
Related Videos
 32:55
32:55Open Source Secure Software Supply Chain in action
Natale Vinto
 26:41
26:41Overcome your trust issues! In a world of fake data, Data Provenance FTW
Jon Geater
 16:00
16:00DevSecOps culture
Ali Yazdani
 51:41
51:41Climate vs. Weather: How Do We Sustainably Make Software More Secure?
Panel Discussion
 26:50
26:50Organizational Change Through The Power Of Why - DevSecOps Enablement
Nazneen Rupawalla
 24:47
24:47Supply Chain Security and the Real World: Lessons From Incidents
Adrian Mouat
 28:45
28:45How your .NET software supply chain is open to attack : and how to fix it
Andrei Epure
 25:48
25:48Reviewing 3rd party library security easily using OpenSSF Scorecard
Niels Tanis
Related Articles
View all articles
.gif?w=240&auto=compress,format)


From learning to earning
Jobs that call for the skills explored in this talk.

SAP AG
Sankt Leon-Rot, Germany
Junior
Go
Azure
DevOps
Puppet
Docker
+6



Siemens AG
Berlin, Germany
C++
GIT
CMake
Linux
DevOps
+7



NTT Data Deutschland SE
München, Germany
Java
DevOps
Python
Node.js
Continuous Integration

The Yellow SiC Holding GmbH
Berlin, Germany
API
C++
DevOps
Python
JavaScript
+1
