Security Operations Center Analyst
Role details
Job location
Tech stack
Job description
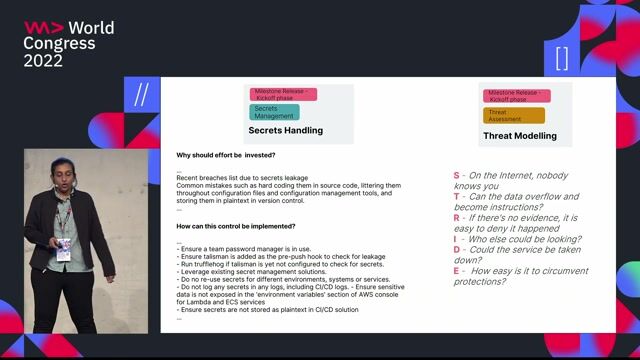
Monitor and investigate alerts leveraging EDR and NDR solutions * Review security events that are populated in a Security Information and Event Management (SIEM) system * Analyze a variety of network and host-based security appliance logs (Firewalls, NIDS, HIDS, Sys Logs, etc.) to determine the correct remediation actions and escalation paths for each incident * Identify the incident root cause and take proactive mitigation steps * Assist with incident response efforts * Follows precise analytical paths to determine the nature and extent of problems being reported by tools, e-mails, alerts, etc. * Integrate and share information with other analysts and other teams * Determine and direct remediation and recovery efforts. * Provide other ad hoc support as required Required Technical Skills * Knowledge of Transmission Control Protocol / Internet Protocol (TCP / IP) protocols * Deep knowledge of Microsoft Security Tools (e.g. M365, Cloud App Security, Azure, Defender for Endpoint
Requirements
Azure Security, Azure Sentinel and XDR) * Deep knowledge of Cloud technologies (e.g. Azure, AWS and GCP) * Deep knowledge of SIEM tools like Splunk, QRadar, ArcSight, MS Sentinel, ELK Stack * Knowledge of at least one EDR solution (MS Defender for Endpoint, SentinelOne, CrowdStrike) * Knowledge of email security, network monitoring, and incident response * Knowledge of Linux / Mac / Windows * A minimum of five (5) years of relevant experience in the information technology field, including triage of alerts and supporting security incidents * Proven experience with the usual toolbox available in a SOC (e.g., SIEMs, EDRs), able to autonomously perform technical analysis of security threats and collaborate with the Incident Response team * Trouble ticket generation and processing experienceExtensive Windows, Linux, Database, Application, Web server, etc. log analysis * Expert knowledge of English, both written and spoken, is required The resource SHOULD have the following skills and experience * Experience on an Incident Response team performing Tier I / II initial incident triage. * Proven knowledge of monitoring AWS environment (IaaS, Saas, Paas) * Knowledge of at least one general-purpose or shell scripting language (e.g. Ruby, Bash, PowerShell, Python, etc.) Required Soft Skills * Excellent communication skills * Customer-facing experience and oral communication skills Ability to write documentation & reports * Creativity / ability to find innovative solutions * Willingness to learn on the job * Conflict management & cooperation Desirable certifications * Technical certifications: MCSE, CCNA, Microsoft Azure (e.g., SC-200), GCIH, CEH, GCFA or any GIAC / similar certification * Relevant industry certifications #J-18808-Ljbffr