Jennifer Reif
Cyber Sleuth: Finding Hidden Connections in Cyber Data
#1about 6 minutes
Understanding the complexity of modern cybersecurity threats
Cybersecurity involves diverse domains and multi-step attack chains that require compiling data from multiple sources to prevent breaches.
#2about 6 minutes
Why attackers think in graphs, not lists
Attackers exploit interconnected pathways to hop between systems, while defenders often focus on static lists of permissions, creating a strategic disadvantage.
#3about 6 minutes
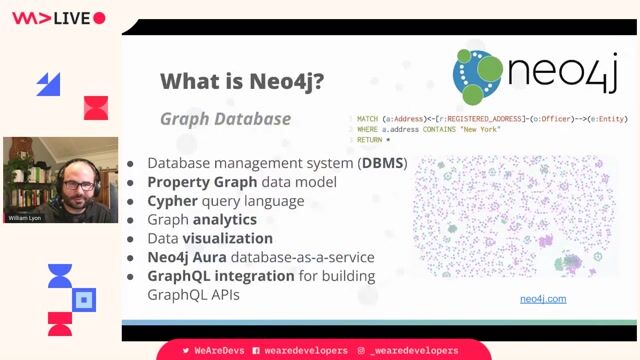
Modeling connected data with graph databases
Graph databases use nodes, relationships, and labels to create a holistic view of a network, making it easier to surface hidden connections.
#4about 6 minutes
Getting started with Neo4j and the Cypher query language
Learn how to load data into Neo4j using dump files or the APOC library and write basic `CREATE` and `MATCH` queries with the Cypher language.
#5about 7 minutes
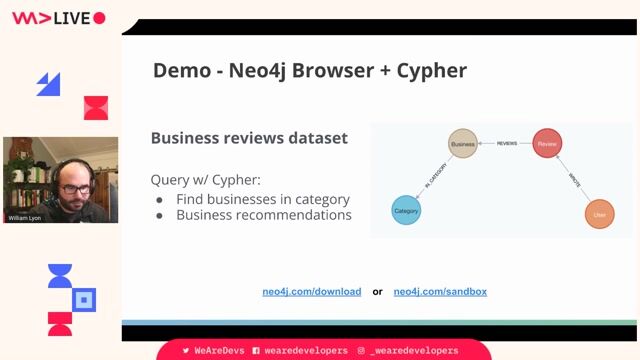
Investigating a user's direct and indirect access
A live demo shows how to use Cypher to trace a user's access from direct machine permissions to multi-hop group memberships.
#6about 5 minutes
Visualizing threats with rule-based styling in Bloom
Use Neo4j Bloom to visually explore the graph with natural language queries and apply rule-based styling with algorithms like PageRank to highlight critical assets.
#7about 5 minutes
Analyzing the blast radius of a compromised account
Discover how to find the shortest attack path to a high-value target and visualize the full blast radius of a single compromised account.
#8about 3 minutes
Resources for learning more about Neo4j
Find resources to continue learning, including a GitHub repository with the dataset, Neo4j sandboxes, and the Graph Academy.
#9about 16 minutes
Q&A on graph databases for cybersecurity
The speaker answers audience questions about required skills, tracking malware, and integrating machine learning with graph databases for threat detection.
Related jobs
Jobs that call for the skills explored in this talk.
ROSEN Technology and Research Center GmbH
Osnabrück, Germany
Senior
TypeScript
React
+3
ROSEN Technology and Research Center GmbH
Lingen (Ems), Germany
Intermediate
Azure
Matching moments

02:41 MIN
An introduction to graph analytics for software systems
Data Science on Software Data

03:20 MIN
Why graph technology was embedded into the Kusto engine
From Tables to Graphs in Minutes: Supercharging Kusto Graph Analytics with AI-Powered Development

06:03 MIN
AI demo for generating cybersecurity graph models
From Tables to Graphs in Minutes: Supercharging Kusto Graph Analytics with AI-Powered Development
03:28 MIN
Understanding graph databases and the Cypher query language
Putting the Graph In GraphQL With The Neo4j GraphQL Library

03:48 MIN
Representing complex data with knowledge graphs
Large Language Models ❤️ Knowledge Graphs
04:34 MIN
Understanding the fundamentals of graph databases
Martin O'Hanlon - Make LLMs make sense with GraphRAG

02:26 MIN
Why developers make basic cybersecurity mistakes
Don't Be A Naive Developer: How To Avoid Basic Cybersecurity Mistakes
06:22 MIN
Querying connected data with Cypher in Neo4j Browser
Putting the Graph In GraphQL With The Neo4j GraphQL Library
Featured Partners
Related Videos
 43:56
43:56Getting under the skin: The Social Engineering techniques
Mauro Verderosa
 2:08:06
2:08:06The attacker's footprint
Antonio de Mello & Amine Abed
 29:34
29:34You can’t hack what you can’t see
Reto Kaeser
 40:38
40:38How to Cause (or Prevent) a Massive Data Breach- Secure Coding and IDOR
Anna Bacher
 37:32
37:32Cyber Security: Small, and Large!
Martin Schmiedecker
 27:32
27:32Security Pitfalls for Software Engineers
Jasmin Azemović
 1:54:28
1:54:28What makes Cybersecurity different for critical infrastructure?
Kurt Eder
 57:47
57:47Cracking the Code: Decoding Anti-Bot Systems!
Fabien Vauchelles
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.



Recorded Future's Insikt Group
Remote
Senior
Bash
Perl
Linux
Python
+2

Deciphex & Our Group
Remote
Senior
Linux
SharePoint
Amazon Web Services (AWS)
Scripting (Bash/Python/Go/Ruby)



aXite Security Tools
Amsterdam, Netherlands
Node.js
Angular
JavaScript

Neo4j, Inc.
Charing Cross, United Kingdom
GIT
Java
Ruby
React
Python
+4

JobRad GmbH
Freiburg im Breisgau, Germany
Senior
GIT
Unix
Linux
Python
Network Security