Martina Kraus
Cross Site Scripting is yesterday's news, isn't it?
#1about 2 minutes
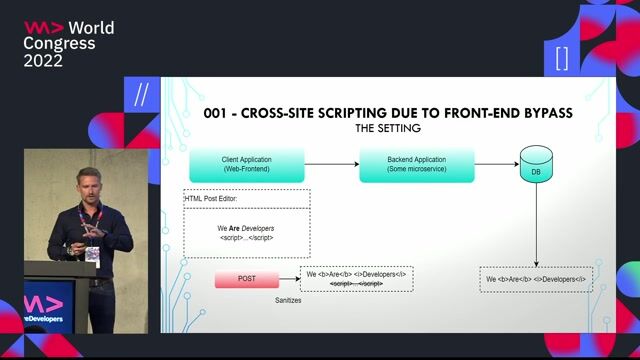
Demonstrating a persistent cross-site scripting attack
A live demo shows how malicious JavaScript can be injected into an input field and stored in a database, executing on every page load.
#2about 3 minutes
Why built-in framework sanitizers are not enough
Framework sanitizers can be bypassed by using native DOM APIs directly, and the vast majority of application code comes from third-party NPM packages.
#3about 4 minutes
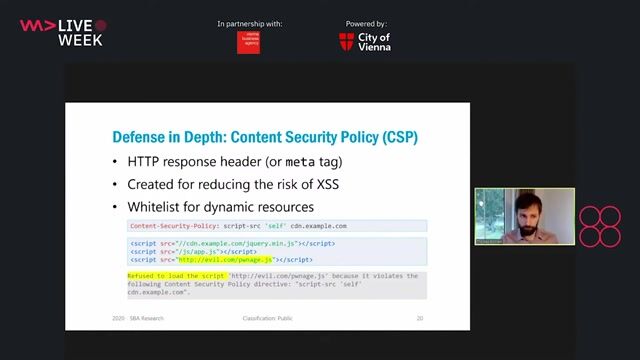
Introducing the Content Security Policy http header
The Content Security Policy (CSP) is an HTTP header that controls which resources can be loaded and executed by the browser using directives for scripts, styles, and API connections.
#4about 4 minutes
Implementing and refining a basic content security policy
A live demo shows how to add a CSP via a meta tag and then iteratively fix broken styles and API calls by adjusting the `style-src` and `connect-src` directives.
#5about 3 minutes
Safely executing inline scripts with hashes and nonces
CSP Level 2 provides hashes and nonces as secure alternatives to `unsafe-inline` for whitelisting specific inline scripts for execution.
#6about 7 minutes
Using CSP nonces with server-side rendering
Nonces must be unique and randomly generated on the server for each request to be secure, and the `strict-dynamic` directive allows trusted scripts to load other scripts.
#7about 3 minutes
Introducing trusted types to secure dangerous dom sinks
Trusted Types is a new CSP directive that locks down dangerous DOM APIs, requiring that any data passed to them must first be sanitized and wrapped in a special trusted object.
#8about 3 minutes
Implementing trusted types with the dompurify library
Instead of writing custom sanitization logic, you can use a library like DOMPurify with its `RETURN_TRUSTED_TYPE` option to easily create secure, trusted HTML objects.
#9about 1 minute
Browser support and final recommendations for trusted types
Trusted Types are currently supported by all Chromium-based browsers, making it a viable defense-in-depth strategy for a significant portion of web users.
Related jobs
Jobs that call for the skills explored in this talk.
Hubert Burda Media
München, Germany
€80-95K
Intermediate
Senior
JavaScript
Node.js
+1
Technoly GmbH
Berlin, Germany
Senior
JavaScript
Angular
+1
Matching moments

04:32 MIN
The primary security threat of cross-site scripting
A Primer in Single Page Application Security (Angular, React, Vue.js)
03:21 MIN
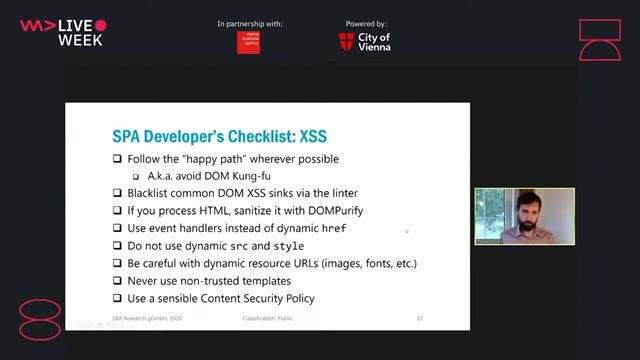
A practical checklist for preventing XSS in SPAs
A Primer in Single Page Application Security (Angular, React, Vue.js)
03:40 MIN
Understanding the real-world danger of cross-site scripting
Securing Frontend Applications with Trusted Types
04:02 MIN
How modern frameworks fail to prevent all XSS attacks
Securing Frontend Applications with Trusted Types
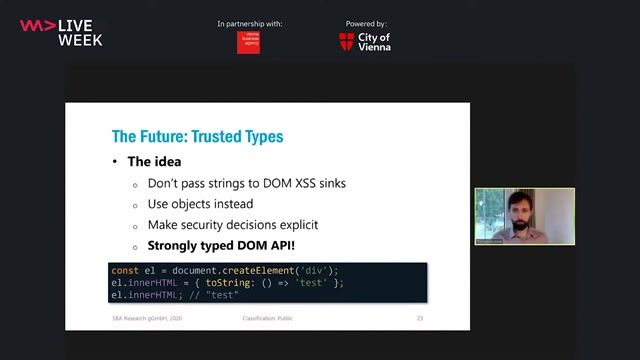
02:15 MIN
The future of XSS prevention with Trusted Types
A Primer in Single Page Application Security (Angular, React, Vue.js)
03:06 MIN
Using Content Security Policy for defense in depth
A Primer in Single Page Application Security (Angular, React, Vue.js)
14:43 MIN
Live demo of exploiting a cross-site scripting vulnerability
Maturity assessment for technicians or how I learned to love OWASP SAMM
03:10 MIN
Preventing XSS by sanitizing on the backend
101 Typical Security Pitfalls
Featured Partners
Related Videos
 45:19
45:19Securing Frontend Applications with Trusted Types
Philippe De Ryck
 36:39
36:39A Primer in Single Page Application Security (Angular, React, Vue.js)
Thomas Konrad
 28:41
28:41101 Typical Security Pitfalls
Alexander Pirker
 26:59
26:59Security in modern Web Applications - OWASP to the rescue!
Jakub Andrzejewski
 29:47
29:47You click, you lose: a practical look at VSCode's security
Thomas Chauchefoin & Paul Gerste
 27:10
27:10Hack-Proof The Node.js runtime: The Mechanics and Defense of Path Traversal Attacks
Sonya Moisset
 27:41
27:41Friend or Foe? TypeScript Security Fallacies
Liran Tal
 44:11
44:11Vulnerable VS Code extensions are now at your front door
Raul Onitza-Klugman & Kirill Efimov
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.

&why GmbH
Berlin, Germany
€50-70K
Junior
Intermediate
Senior
React
Next.js
TypeScript

aXite Security Tools
Amsterdam, Netherlands
Node.js
Angular
JavaScript

Mendix
Rotterdam, Netherlands
Remote
Intermediate
React
low-code
TypeScript
Continuous Integration

Content Pass GmbH
Berlin, Germany
Senior
API
Node.js
JavaScript
TypeScript
Continuous Integration

![01 / 11 / 25 - 01 / 01 / 30 ActiveXchange Sport Data - Full Stack Developer (Angular / .NET / SQL) | Remote[...]](https://wearedevelopers.imgix.net/public/default-job-listing-cover.png?w=400&ar=3.55&fit=crop&crop=entropy&auto=compress,format)
Protospace
Remote
£50-70K
Intermediate
API
GIT
.NET
+6

Anexia Cloud Solutions GmbH
Klagenfurt am Wörthersee, Austria
€54K
Nginx
React
DevOps
Docker
+5

X-on Health
Eaton, United Kingdom
£50K
Senior
CSS
SASS
Scrum
React
+3
