Liran Tal
Friend or Foe? TypeScript Security Fallacies
#1about 2 minutes
The common misconception of TypeScript as a security tool
Developers often mistakenly believe TypeScript's type safety provides runtime security, but it is a development-time tool that doesn't prevent real-world attacks.
#2about 3 minutes
How HTTP parameter pollution creates ambiguity
Attackers can exploit how backends handle duplicate or malformed query parameters to cause unexpected behavior and bypass security checks.
#3about 5 minutes
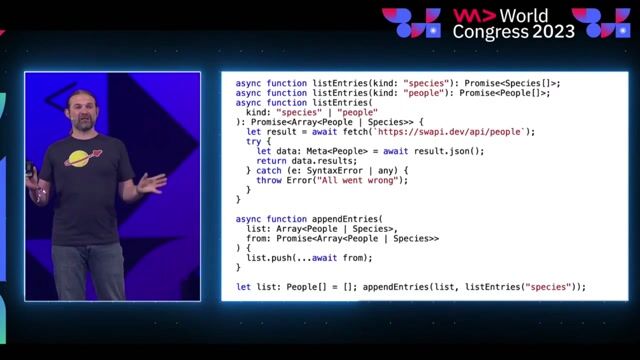
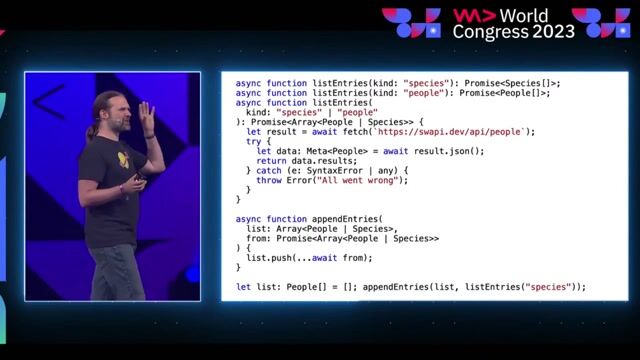
Bypassing TypeScript types and interfaces with type juggling
Simple type definitions like `any`, explicit string casting, and even interfaces can be bypassed by sending array-like parameters, leading to vulnerabilities like cross-site scripting (XSS).
#4about 3 minutes
Why TypeScript is a dev-time tool, not a runtime guardrail
TypeScript checks are stripped out at compile time and have no effect on the running application, necessitating runtime validation techniques like type narrowing.
#5about 7 minutes
Exploiting prototype pollution to bypass Zod schema validation
Even with a schema validation library like Zod, attackers can use specially crafted payloads with `__proto__` to pollute the global Object prototype and gain unauthorized privileges.
#6about 2 minutes
Using mass assignment to bypass Zod's default behavior
By default, Zod allows extra, undefined properties in an object, which can lead to mass assignment vulnerabilities when the object is passed to an ORM.
#7about 2 minutes
Real-world examples of parameter pollution vulnerabilities
Popular libraries like object-path and the EJS templating engine have been vulnerable to parameter pollution, demonstrating how these attacks affect real applications.
#8about 2 minutes
Why TypeScript is like code coverage, not a security guarantee
Relying solely on TypeScript for security is like trusting 100% code coverage for bug-free code; it's a helpful tool but not a substitute for dedicated security practices.
Related jobs
Jobs that call for the skills explored in this talk.
Eltemate
Amsterdam, Netherlands
Intermediate
Senior
TypeScript
Continuous Integration
+1
Hubert Burda Media
München, Germany
€80-95K
Intermediate
Senior
JavaScript
Node.js
+1
Matching moments

01:42 MIN
Applying typed security to OWASP vulnerabilities
Typed Security: Preventing Vulnerabilities By Design
01:39 MIN
The hidden dangers in everyday TypeScript code
Lies we Tell Ourselves As Developers

04:07 MIN
Evaluating the strengths and limitations of TypeScript
Don't compromise on speedy delivery nor type-safety by choosing TypeScript

02:26 MIN
Why developers make basic cybersecurity mistakes
Don't Be A Naive Developer: How To Avoid Basic Cybersecurity Mistakes

02:11 MIN
Understanding the power and popularity of TypeScript
End-to-End TypeScript: Completing the Modern Development Stack
02:37 MIN
Understanding TypeScript's origins and role in scalability
All you need is types

04:30 MIN
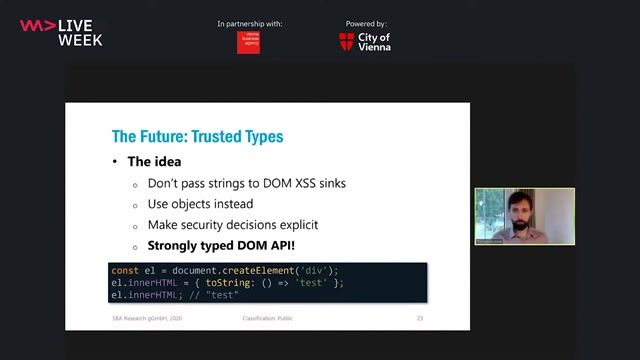
Using Trusted Types in development to secure all browsers
Securing Frontend Applications with Trusted Types
02:15 MIN
The future of XSS prevention with Trusted Types
A Primer in Single Page Application Security (Angular, React, Vue.js)
Featured Partners
Related Videos
 31:13
31:13Lies we Tell Ourselves As Developers
Stefan Baumgartner
 58:19
58:19Typed Security: Preventing Vulnerabilities By Design
Michael Koppmann
 29:44
29:44Don't compromise on speedy delivery nor type-safety by choosing TypeScript
Jens Claes
 29:17
29:17End-to-End TypeScript: Completing the Modern Development Stack
Marco Podien
 26:59
26:59Security in modern Web Applications - OWASP to the rescue!
Jakub Andrzejewski
 45:19
45:19Securing Frontend Applications with Trusted Types
Philippe De Ryck
 28:41
28:41101 Typical Security Pitfalls
Alexander Pirker
 30:54
30:54Cross Site Scripting is yesterday's news, isn't it?
Martina Kraus
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.

Confideck GmbH
Vienna, Austria
Remote
Intermediate
Senior
Node.js
MongoDB
TypeScript


aXite Security Tools
Amsterdam, Netherlands
Node.js
Angular
JavaScript

nono
£75-120K
Intermediate
API
Node.js
Grafana
GraphQL
+9

Client Server
Charing Cross, United Kingdom
Remote
£90-110K
API
React
TypeScript
+4

United Kingdom - 2 minutes ago
Intermediate
API
GIT
Azure
React
Python
+6

Client Server
Charing Cross, United Kingdom
Remote
£90-100K
Senior
API
React
Node.js
+5

Provectus
Remote
API
GIT
JSON
REST
+11
