Natale Vinto
Open Source Secure Software Supply Chain in action
#1about 2 minutes
Understanding the rising threat to software supply chains
The dramatic increase in supply chain attacks necessitates new security standards and government regulations to mitigate risk.
#2about 2 minutes
Exploring the core domains of supply chain security
Securing the supply chain involves understanding software composition with SBOMs, continuous scanning, content signing, and runtime policy enforcement.
#3about 5 minutes
Using open source tools to secure the entire SDLC
A suite of open source tools like Sigstore, Tecton, and Clair can be used to prevent malicious code, safeguard build systems, and monitor deployments.
#4about 2 minutes
Defining key standards and terminology in supply chain security
Understanding critical concepts like SALSA levels, CVEs, provenance, attestation, and SBOMs is essential for implementing robust security.
#5about 3 minutes
Building a secure and opinionated CI/CD pipeline
A secure pipeline can be constructed using Tecton for SALSA compliance and Sigstore for keyless signing of commits and artifacts.
#6about 4 minutes
Comparing a generic vs a security-augmented workflow
A security-augmented workflow integrates checks like local dependency scanning, commit signature verification, and SALSA compliance into the standard development process.
#7about 4 minutes
Demo: Initiating a secure code update for an application
The demonstration begins by scaffolding a microservice from a secure software template and making a code change to update inventory.
#8about 3 minutes
Demo: Scanning and remediating vulnerabilities locally in the IDE
Using an IDE extension, transitive dependencies are scanned for vulnerabilities, which are then fixed by updating the framework and base image versions.
#9about 4 minutes
Demo: Triggering the secure pipeline with a keyless signed commit
The developer uses keyless signing with an OIDC provider to sign the commit, which automatically triggers a secure pipeline that verifies the signature and generates an SBOM.
#10about 3 minutes
Demo: Verifying deployment and monitoring runtime security
The demo concludes by showing the successfully deployed application and using a security dashboard to check for runtime policy violations and visualize network traffic.
Related jobs
Jobs that call for the skills explored in this talk.
ROSEN Technology and Research Center GmbH
Osnabrück, Germany
Senior
TypeScript
React
+3
VECTOR Informatik
Stuttgart, Germany
Senior
Kubernetes
Terraform
+1
IGEL Technology GmbH
Bremen, Germany
Senior
Java
IT Security
Matching moments
04:45 MIN
Mitigating supply chain attacks with DevSecOps practices
Security Pitfalls for Software Engineers
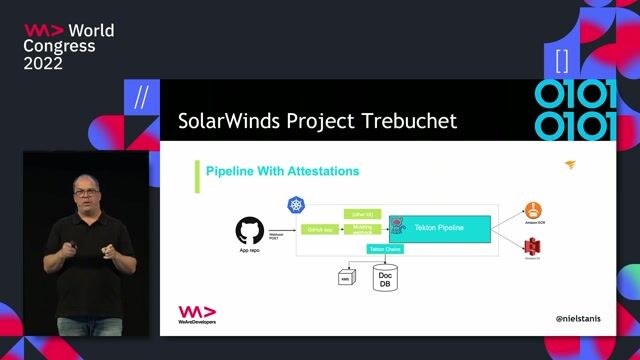
02:25 MIN
Implementing and enforcing supply chain policies
Securing your application software supply-chain
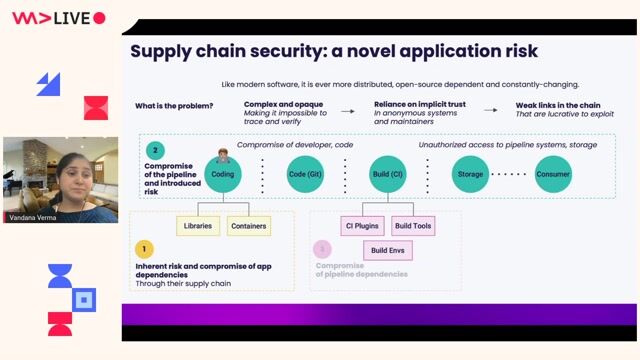
03:50 MIN
Building a foundation for pipeline security
Walking into the era of Supply Chain Risks

10:01 MIN
Taking responsibility for your software supply chain
Coffee with Developers with Feross Aboukhadijeh of Socket about the xz backdoor

06:19 MIN
Understanding the risks of the modern software supply chain
Overcome your trust issues! In a world of fake data, Data Provenance FTW

04:14 MIN
The scale and challenge of securing open source
How GitHub secures open source
02:53 MIN
Defining the modern software supply chain
Securing your application software supply-chain

01:52 MIN
Securing container images and the software supply chain
Security Challenges of Breaking A Monolith
Featured Partners
Related Videos
 28:27
28:27Securing your application software supply-chain
Niels Tanis
 26:41
26:41Overcome your trust issues! In a world of fake data, Data Provenance FTW
Jon Geater
 16:00
16:00DevSecOps culture
Ali Yazdani
 26:50
26:50Organizational Change Through The Power Of Why - DevSecOps Enablement
Nazneen Rupawalla
 1:58:59
1:58:59Stranger Danger: Your Java Attack Surface Just Got Bigger
Vandana Verma Sehgal
 58:57
58:57Securing Secrets in the GitOps era
Alex Soto
 24:47
24:47Supply Chain Security and the Real World: Lessons From Incidents
Adrian Mouat
 25:28
25:28How GitHub secures open source
Joseph Katsioloudes
Related Articles
View all articles


.gif?w=240&auto=compress,format)
From learning to earning
Jobs that call for the skills explored in this talk.


Kenos Technology
Málaga, Spain
Senior
DevOps
Openshift
Kubernetes
Continuous Integration

SAP AG
Sankt Leon-Rot, Germany
Junior
Go
Azure
DevOps
Puppet
Docker
+6


KLETA
Paris, France
DevOps
Terraform
Continuous Integration
Amazon Web Services (AWS)


Siemens AG
Berlin, Germany
C++
GIT
CMake
Linux
DevOps
+7

Seidor Gesein
Remote
€104K
DevOps
Terraform
Agile Methodologies
