Marcel Lupo
Best Practices for Using GitHub Secrets
#1about 2 minutes
Understanding the fundamentals of GitHub Secrets
GitHub Secrets provide an encrypted way to store sensitive data like API keys within repositories for use in CI/CD workflows.
#2about 6 minutes
Managing secrets at different scopes in the UI
Secrets can be managed at the repository, environment, or organization level through the UI, but repository-level secrets become difficult to rotate at scale.
#3about 5 minutes
Consuming secrets in workflows and avoiding common pitfalls
Reference secrets in GitHub Actions using the `secrets` context, but be aware of pitfalls like hard-coding, commit history exposure, and improper access control.
#4about 5 minutes
Integrating GitHub with Azure Key Vault for centralization
Use Azure Key Vault as a centralized secret store to manage secrets outside of GitHub, improving scalability and separating access controls.
#5about 7 minutes
Configuring passwordless authentication using OpenID Connect
Set up a federated identity in Azure Entra ID with OpenID Connect to allow GitHub Actions to authenticate to Azure without long-lived secrets.
#6about 7 minutes
Fetching Azure Key Vault secrets in a GitHub workflow
Use the `azure/login` action with OIDC to authenticate, then use Azure CLI within a workflow to retrieve secrets from Key Vault for subsequent steps.
#7about 4 minutes
Key benefits of the Azure Key Vault integration
Integrating with Azure Key Vault provides centralized management, granular RBAC, secret versioning and history, and enhanced auditing capabilities.
Related jobs
Jobs that call for the skills explored in this talk.
ROSEN Technology and Research Center GmbH
Osnabrück, Germany
Senior
TypeScript
React
+3
IGEL Technology GmbH
Bremen, Germany
Senior
Java
IT Security
VECTOR Informatik
Stuttgart, Germany
Senior
Kubernetes
Terraform
+1
Matching moments
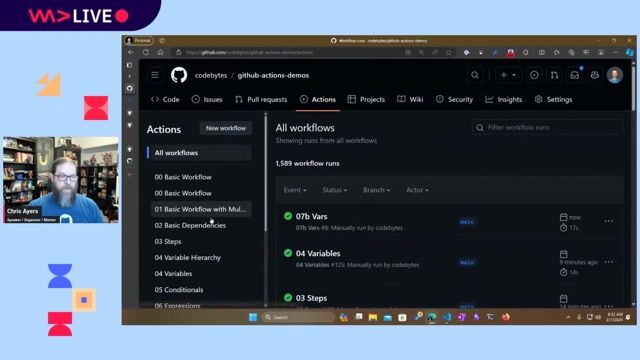
02:32 MIN
Securing workflows with secrets and best practices
CI/CD with Github Actions

07:11 MIN
Why hard-coded secrets are a growing developer problem
Stop Committing Your Secrets - GIt Hooks To The Rescue!

15:37 MIN
Key takeaways for preventing secret leaks in code
Stop Committing Your Secrets - GIt Hooks To The Rescue!
03:59 MIN
Using Azure for secure configuration and secrets management
Develop enterprise-ready applications for Microsoft Teams with Azure resources on modern web technologies

03:42 MIN
Securely handing over credentials and application secrets
SRE Methods In an Agency Environment
02:45 MIN
Key takeaways for securing your application pipeline
Securing Your Web Application Pipeline From Intruders
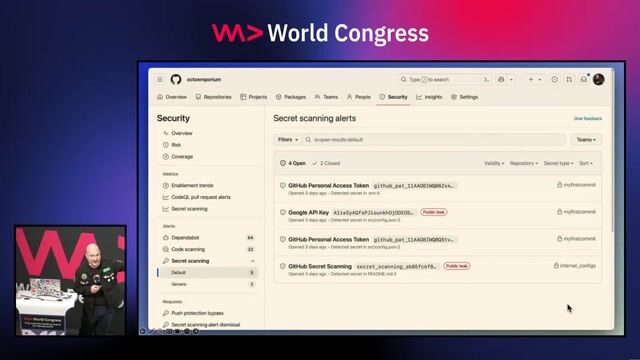
02:42 MIN
Prevent leaked secrets with push protection and scanning
Real-World Security for Busy Developers
18:28 MIN
Q&A on GitOps secret management practices
Securing secrets in the GitOps Era
Featured Partners
Related Videos
 58:52
58:52Securing secrets in the GitOps Era
Davide Imola
 58:57
58:57Securing Secrets in the GitOps era
Alex Soto
 1:05:06
1:05:06CI/CD with Github Actions
Chris Ayers
 1:04:54
1:04:54Lights, Camera, GitHub Actions!
Ixchel Ruiz
 56:06
56:06Stop Committing Your Secrets - GIt Hooks To The Rescue!
Dwayne McDaniel
 29:50
29:50Real-World Security for Busy Developers
Kevin Lewis
 30:07
30:07External Secrets Operator: the secrets management toolbox for self-sufficient teams
Moritz Johner
 25:28
25:28How GitHub secures open source
Joseph Katsioloudes
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.

Seidor Gesein
Remote
€104K
DevOps
Terraform
Agile Methodologies

amaxo GmbH
Remote
€87K
Senior
Azure
DevOps
Terraform
+2





Michael Bailey Associates
Bern, Switzerland
API
DevOps
Gitlab
Docker
Ansible
+6


Governikus GmbH & Co. KG
Köln, Germany
Remote
Linux
DevOps
Continuous Integration
Configuration Management