Andrew Martin
Hacking Kubernetes: Live Demo Marathon
#1about 8 minutes
Understanding the Kubernetes threat landscape and adversaries
Threat modeling helps build appropriate security controls by identifying potential adversaries, from script kiddies to organized crime.
#2about 3 minutes
Demonstrating a supply chain attack using NPM hooks
A malicious NPM package can use a preinstall hook to execute arbitrary code and exfiltrate sensitive files like SSH or cloud keys from a developer's machine.
#3about 12 minutes
Gaining a reverse shell through pod misconfigurations
An attacker can gain a reverse shell and break out of a container by exploiting pod misconfigurations like privileged mode and sharing the host PID namespace.
#4about 9 minutes
Executing a container breakout using the Dirty Pipe vulnerability
The Dirty Pipe vulnerability allows an unprivileged user to overwrite root-owned files, enabling a container breakout by patching the runc binary in memory.
#5about 7 minutes
Pivoting post-breakout to steal secrets from other pods
After gaining root on a node, an attacker can pivot by enumerating the host filesystem to find and steal secrets mounted into other pods running on the same node.
#6about 5 minutes
Using canary tokens as a last line of defense
Embedding canary tokens, which are credentials with no permissions, provides a tripwire that triggers an intrusion detection alert when an attacker attempts to use them.
Related jobs
Jobs that call for the skills explored in this talk.
VECTOR Informatik
Stuttgart, Germany
Senior
Kubernetes
Terraform
+1
Power Plus Communications
Mannheim, Germany
Intermediate
Senior
Docker
Kubernetes
+1
Wilken GmbH
Ulm, Germany
Senior
Amazon Web Services (AWS)
Kubernetes
+1
Matching moments
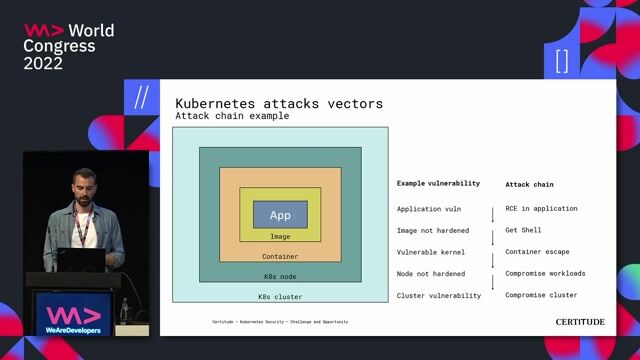
02:06 MIN
Deconstructing a typical Kubernetes cluster attack chain
Kubernetes Security - Challenge and Opportunity
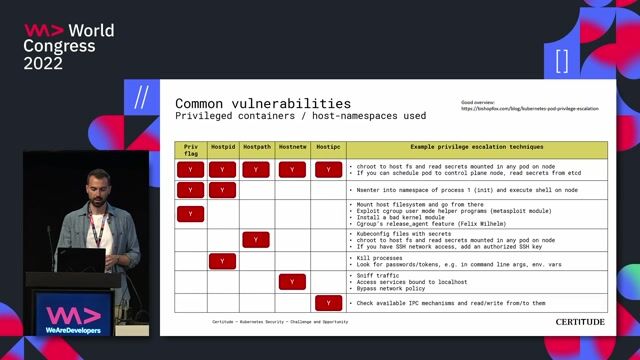
04:28 MIN
Identifying common Kubernetes security vulnerabilities
Kubernetes Security - Challenge and Opportunity
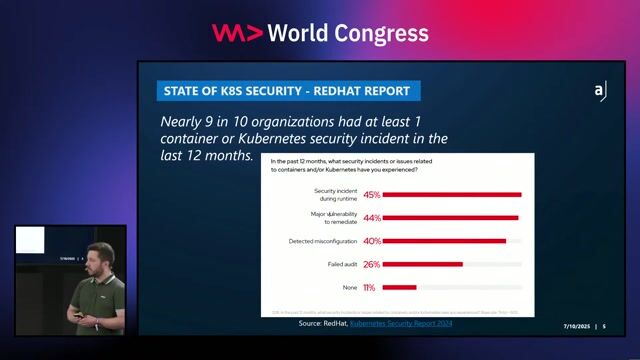
01:27 MIN
The prevalence and impact of Kubernetes security incidents
Kubernetes Security Best Practices
06:25 MIN
Security best practices for containers and Kubernetes
Microservices: how to get started with Spring Boot and Kubernetes
02:52 MIN
Q&A on managed Kubernetes security in the cloud
Kubernetes Security - Challenge and Opportunity
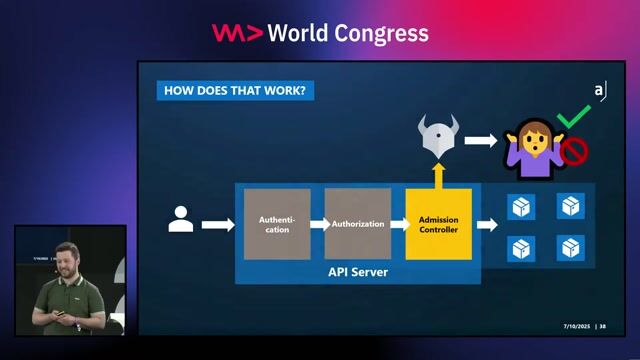
02:16 MIN
Key takeaways for hardening Kubernetes clusters
Kubernetes Security Best Practices

03:01 MIN
Tools and techniques for Kubernetes development
How I saved 200K/yr in direct costs writing 0 code lines in K8s
07:59 MIN
Securing containers and infrastructure as code (IAC)
Maturity assessment for technicians or how I learned to love OWASP SAMM
Featured Partners
Related Videos
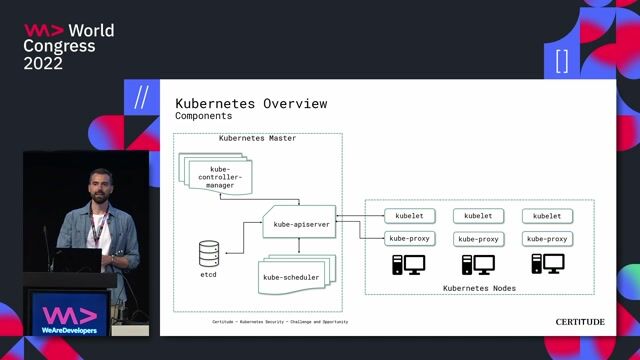 42:45
42:45Kubernetes Security - Challenge and Opportunity
Marc Nimmerrichter
 44:00
44:00Enhancing Workload Security in Kubernetes
Dimitrij Klesev & Andreas Zeissner
 40:00
40:00Local Development Techniques with Kubernetes
Rob Richardson
 23:08
23:08Kubernetes Security Best Practices
Rico Komenda
 28:47
28:47Turning Container security up to 11 with Capabilities
Mathias Tausig
 28:36
28:36What we Learned from Reading 100+ Kubernetes Post-Mortems
Noaa Barki
 57:24
57:24Mastering Kubernetes – Beginner Edition
Hannes Norbert Göring
 27:52
27:52Chaos in Containers - Unleashing Resilience
Maish Saidel-Keesing
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.






virtual7 GmbH
Mainz, Germany
Senior
DevOps
Docker
Openshift
Kubernetes
Agile Methodologies
+1

virtual7 GmbH
Köln, Germany
Senior
DevOps
Docker
Openshift
Kubernetes
Agile Methodologies
+1

virtual7 GmbH
Hamburg, Germany
Senior
DevOps
Docker
Openshift
Kubernetes
Agile Methodologies
+1

virtual7 GmbH
Düsseldorf, Germany
Senior
DevOps
Docker
Openshift
Kubernetes
Agile Methodologies
+1