Mathias Tausig
Turning Container security up to 11 with Capabilities
#1about 8 minutes
Demonstrating a man-in-the-middle attack between containers
A proof-of-concept shows how a malicious container can sniff unencrypted traffic between other containers running on the same host.
#2about 5 minutes
Introducing Linux capabilities for granular privilege control
Traditional Unix permissions are an all-or-nothing model, whereas Linux capabilities split root privileges into distinct units for finer control.
#3about 4 minutes
Differentiating between file and process capabilities
Capabilities can be set on files to elevate privileges for specific binaries or on processes to reduce them, with the latter being key for containers.
#4about 3 minutes
Managing default container capabilities in Docker
Docker grants a default set of powerful capabilities to containers, which can be restricted using `cap-drop` and `cap-add` flags.
#5about 4 minutes
Securing deployments by dropping unnecessary capabilities
By dropping all capabilities and only adding back the essential ones, the man-in-the-middle attack is successfully prevented in both Docker and Kubernetes.
#6about 3 minutes
Using capabilities as a defense-in-depth measure
Limiting capabilities does not prevent an initial exploit but significantly reduces the potential impact and blast radius of a compromised container.
Related jobs
Jobs that call for the skills explored in this talk.
VECTOR Informatik
Stuttgart, Germany
Senior
Kubernetes
Terraform
+1
ROSEN Technology and Research Center GmbH
Osnabrück, Germany
Senior
TypeScript
React
+3
Power Plus Communications
Mannheim, Germany
Intermediate
Senior
Docker
Kubernetes
+1
Matching moments
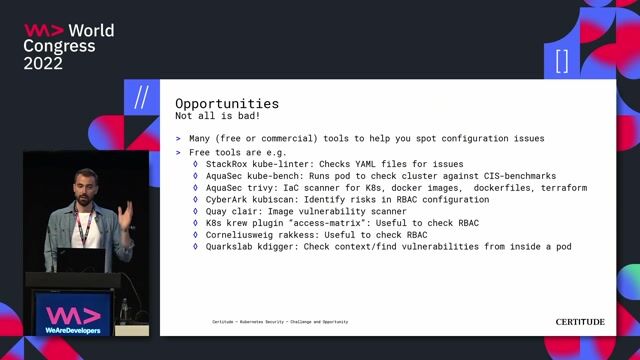
01:22 MIN
Leveraging containerization for improved security posture
Kubernetes Security - Challenge and Opportunity
06:25 MIN
Security best practices for containers and Kubernetes
Microservices: how to get started with Spring Boot and Kubernetes

01:52 MIN
Securing container images and the software supply chain
Security Challenges of Breaking A Monolith

02:30 MIN
Securing container images against common vulnerabilities
Kubernetes Security Best Practices
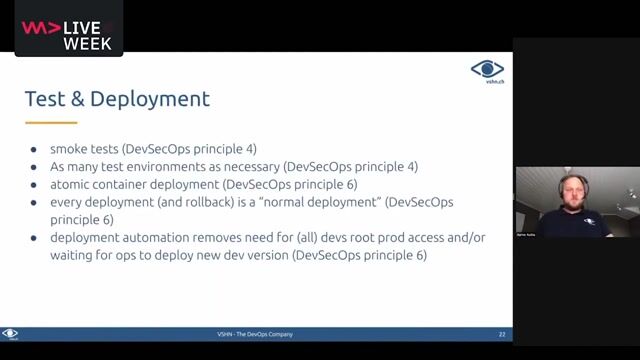
02:35 MIN
Using containers to improve security and deployment
DevSecOps: Security in DevOps
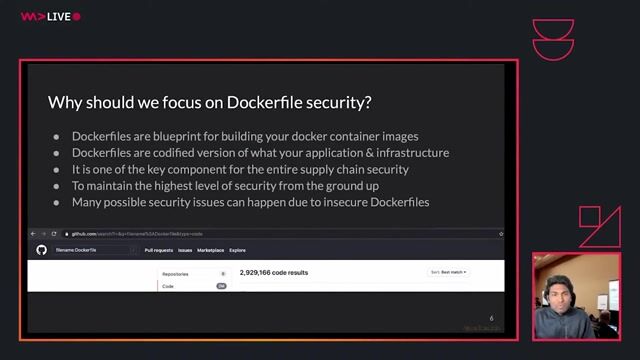
01:35 MIN
Why Dockerfile security is a critical foundation
A practical guide to writing secure Dockerfiles

05:08 MIN
Analyzing the impact of a container vulnerability
Security Challenges of Breaking A Monolith
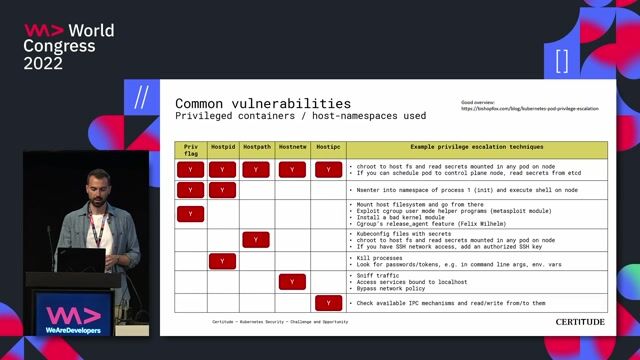
04:28 MIN
Identifying common Kubernetes security vulnerabilities
Kubernetes Security - Challenge and Opportunity
Featured Partners
Related Videos
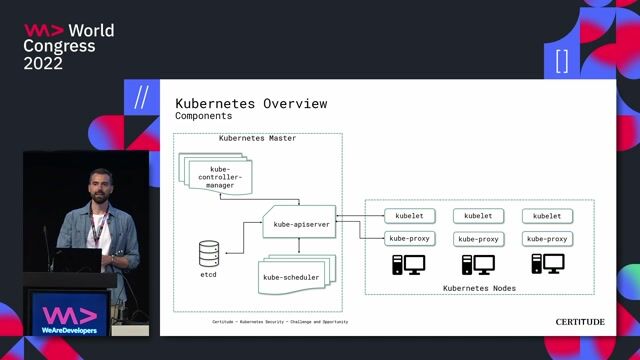 42:45
42:45Kubernetes Security - Challenge and Opportunity
Marc Nimmerrichter
 46:36
46:36Hacking Kubernetes: Live Demo Marathon
Andrew Martin
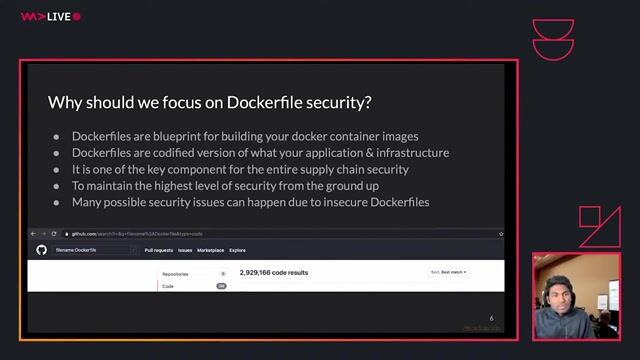 42:25
42:25A practical guide to writing secure Dockerfiles
Madhu Akula
 44:00
44:00Enhancing Workload Security in Kubernetes
Dimitrij Klesev & Andreas Zeissner
 30:33
30:33A solution to embed container technologies into automotive environments
Falk Langer & Lukas Stahlbock
 40:00
40:00Local Development Techniques with Kubernetes
Rob Richardson
 32:55
32:55Open Source Secure Software Supply Chain in action
Natale Vinto
 43:39
43:39Reusing apps between teams and environments through Containers
Adrian Kosmaczewski
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.

Softwarezentrum Böblingen/Sindelfingen e.V.
Böblingen, Germany
Remote
Intermediate
GIT
Bash
Azure
Linux
+5



Ippen.media Gehã¶rt
Kassel, Germany
Linux
DevOps
Docker
VMware
Continuous Delivery

CONTARGO
Duisburg, Germany
Remote
Scrum
DevOps
Gitlab
Puppet
+4

SAP AG
Sankt Leon-Rot, Germany
Junior
Go
Azure
DevOps
Puppet
Docker
+6

SVA System Vertrieb Alexander GmbH
DevOps
Ansible
Openshift
Terraform
Kubernetes
+1

Rocken AG
Zürich, Switzerland
Linux
DevOps
Openshift
Kubernetes
Elasticsearch
+1
