Alvaro Navarro
No More Post-its: Boost your login security with APIs
#1about 5 minutes
Understanding the vulnerabilities of password-based authentication
Passwords are a major security risk because they are easily forgotten, guessed, or cracked, as demonstrated by common password lists and data breaches.
#2about 2 minutes
Implementing two-factor authentication with the Verify API
Add an extra layer of security by implementing two-factor authentication (2FA) using one-time passwords (OTP) delivered via SMS, voice, or other channels with an API.
#3about 2 minutes
Verifying phone numbers and preventing SIM swap attacks
Ensure the phone number receiving an OTP is valid and protect against SIM swap fraud by checking for recent SIM card changes using dedicated APIs.
#4about 2 minutes
Creating a seamless login with silent authentication
Authenticate users frictionlessly in the background by verifying their identity through their mobile data connection and SIM card without requiring manual input.
#5about 2 minutes
Using biometrics and location as authentication factors
Incorporate advanced authentication factors like biometrics for "something you are" and geolocation for "somewhere you are" to further enhance security.
#6about 2 minutes
A summary of APIs for multi-layered security
A recap of the various APIs available to build a robust, multi-layered authentication system covering what you know, have, are, and where you are.
Related jobs
Jobs that call for the skills explored in this talk.
IGEL Technology GmbH
Bremen, Germany
Senior
Java
IT Security
VECTOR Informatik
Stuttgart, Germany
Senior
Java
IT Security
Matching moments
05:18 MIN
Live demo of preventing fraud with identity APIs
Code meets connectivity - Developers as the powerhouse of Network API innovation

05:58 MIN
Using network APIs for identity and fraud prevention
Opening the Mobile Space with CAMARA’s Network APIs - CAMARA Project
06:07 MIN
Exploring practical use cases for network APIs
Opening the Mobile Space with CAMARA’s Network APIs - CAMARA Project
04:34 MIN
Securing accounts with multi-factor authentication layers
Going Beyond Passwords: The Future of User Authentication
03:02 MIN
The fundamental problems with password-based authentication
Passwordless future: WebAuthn and Passkeys in practice

03:15 MIN
Improving user onboarding with silent phone verification
Unleash the power of 5G in your code: transform your apps
01:33 MIN
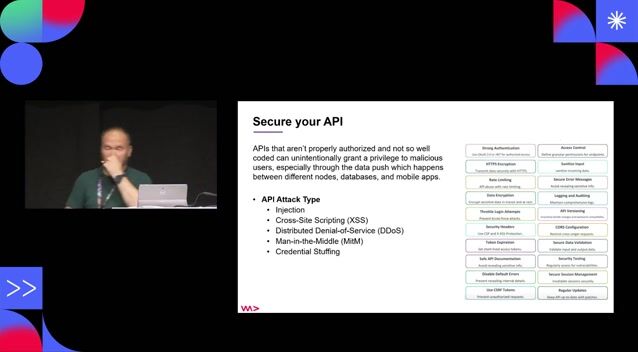
Essential security measures for protecting public APIs
Security Pitfalls for Software Engineers
02:58 MIN
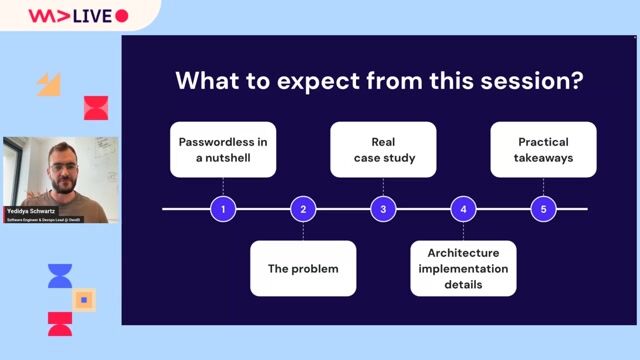
Understanding passwordless authentication technologies
Accelerating Authentication Architecture: Taking Passwordless to the Next Level
Featured Partners
Related Videos
 30:21
30:21Passwordless Web 1.5
Paweł Łukaszuk
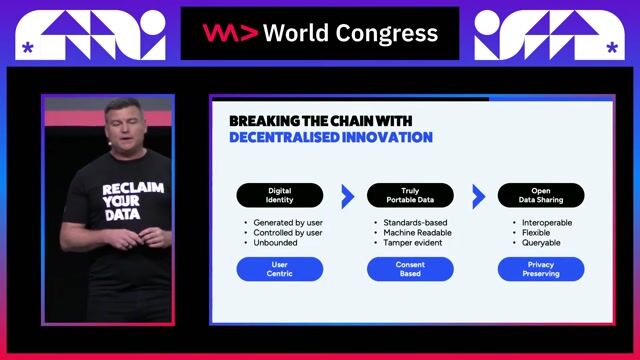 29:31
29:31Break the Chain: Decentralized solutions for today’s Web2.0 privacy problems
Adam Larter
 57:47
57:47Cracking the Code: Decoding Anti-Bot Systems!
Fabien Vauchelles
 27:55
27:55Going Beyond Passwords: The Future of User Authentication
Gift Egwuenu
 31:19
31:19Skynet wants your Passwords! The Role of AI in Automating Social Engineering
Wolfgang Ettlinger & Alexander Hurbean
 32:32
32:32Passwordless future: WebAuthn and Passkeys in practice
Clemens Hübner
 47:34
47:34Architecting API Security
Philippe De Ryck
 33:29
33:29Programming secure C#/.NET Applications: Dos & Don'ts
Sebastian Leuer
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.


Affirm
La Guancha, Spain
Remote
€85-115K
Senior
Python
Amazon Web Services (AWS)



Atruvia AG
Aschheim, Germany
€60-88K
Senior
Linux

Affirm
La Guancha, Spain
Remote
€70-90K
Senior
API
JIRA
Python
+4



Atruvia AG
Karlsruhe, Germany
Remote
€60-88K
Senior
REST
Linux