Reinhard Kugler
A Hitchhikers Guide to Container Security - Automotive Edition 2024
#1about 2 minutes
Recalling a famous remote car hack from 2015
A historical remote car hack demonstrates how attackers gained control over vehicle functions by pivoting from the infotainment system.
#2about 4 minutes
Shifting from distributed ECUs to centralized computers
The automotive industry is moving from a complex network of individual electronic control units (ECUs) to centralized high-performance computers (HPCs) to simplify updates and maintenance.
#3about 6 minutes
Running containers with access to vehicle electronics
A live demonstration shows how a containerized application can directly access and manipulate a car's internal network to control components like the instrument cluster.
#4about 5 minutes
Using eBPF to observe and secure container networking
eBPF programs can be attached to the Linux kernel to observe and filter a container's network traffic at a low level without requiring a sidecar.
#5about 2 minutes
Securing hardware update channels with eBPF policies
eBPF can trace and block unauthorized write operations to hardware interfaces like the SPI bus, preventing malicious firmware flashing from a compromised container.
#6about 2 minutes
Understanding the offensive potential of eBPF rootkits
eBPF is a dual-use technology that can also be used to create stealthy, in-memory rootkits capable of modifying network packets on the fly.
Related jobs
Jobs that call for the skills explored in this talk.
IGEL Technology GmbH
Bremen, Germany
Senior
Java
IT Security
VECTOR Informatik
Stuttgart, Germany
Senior
Java
IT Security
Dirk Rossmann GmbH
Burgwedel, Germany
Intermediate
IT Security
Matching moments

06:39 MIN
New threats from modern vehicle E/E architectures
Automotive Security Challenges: A Supplier's View
03:18 MIN
Q&A on securing CAN bus and future architectures
Cybersecurity for Software Defined Vehicles
05:52 MIN
Applying containerization and immutable OS concepts to cars
The best of two worlds - Bringing enterprise-grade Linux to the vehicle
07:51 MIN
An overview of the automotive security landscape
Automotive Security Challenges: A Supplier's View
04:00 MIN
Exploring the security vulnerabilities of connected cars
Using all the HTML, Running State of the Browser and "Modern" is Rubbish
01:57 MIN
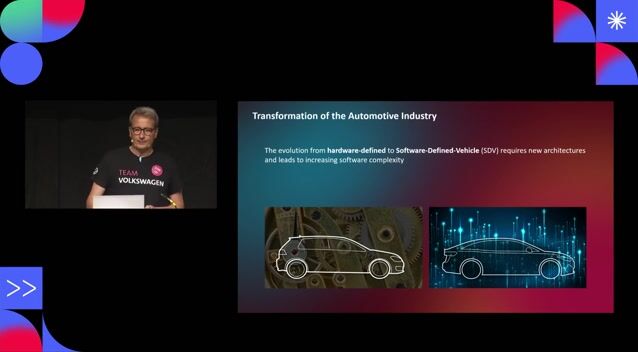
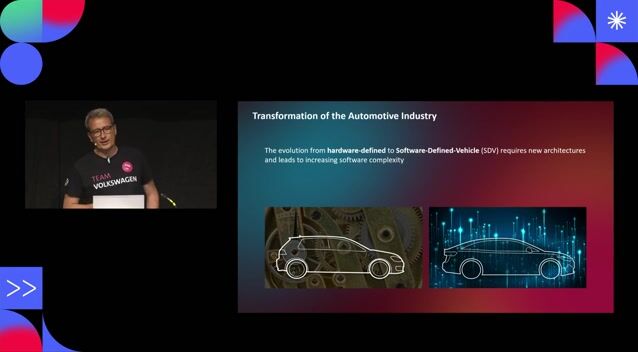
The automotive industry's shift to software-defined vehicles
Cybersecurity for Software Defined Vehicles
04:07 MIN
Navigating the challenges of automotive safety certification
The best of two worlds - Bringing enterprise-grade Linux to the vehicle
07:39 MIN
Integrating autonomous software into complex vehicle hardware
How to develop an autonomous car end-to-end: Robotic Drive and the mobility revolution
Featured Partners
Related Videos
 22:09
22:09Cybersecurity for Software Defined Vehicles
Henning Harbs
 28:20
28:20Into the hive of eBPF!
Mohammed Aboullaite
 30:33
30:33A solution to embed container technologies into automotive environments
Falk Langer & Lukas Stahlbock
 41:03
41:03The best of two worlds - Bringing enterprise-grade Linux to the vehicle
Joachim Werner
 58:59
58:59Automotive Security Challenges: A Supplier's View
Davor Frkat
 37:32
37:32Cyber Security: Small, and Large!
Martin Schmiedecker
 28:47
28:47Turning Container security up to 11 with Capabilities
Mathias Tausig
 21:47
21:47Car's are Technology on Wheels - Impact of Software and IT Competence in Automotive
Rahima Yakoob
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.

Prognum Automotive GmbH
Stuttgart, Germany
Remote
C++

EVA Fahrzeugtechnik GmbH
Krakow am See, Germany
C++
Azure
Python
Amazon Web Services (AWS)

Prognum Automotive GmbH
Ulm, Germany
Remote
C++

Bright Consulting GmbH
Stuttgart, Germany

VISION Consulting GmbH
Raaba, Austria
€55K
Intermediate

advanced engineering GmbH
Remote
Network Security



TECCON Consulting & Engineering GmbH
Graz, Austria
€55K
Intermediate