Rico Komenda
Kubernetes Security Best Practices
#1about 1 minute
The prevalence and impact of Kubernetes security incidents
Most organizations have experienced a Kubernetes security incident in the last year, commonly caused by runtime issues or cluster misconfigurations.
#2about 2 minutes
Applying the 4 Cs model to cloud native security
The 4 Cs model provides a framework for securing the entire stack, from the cloud infrastructure and cluster to the container and code.
#3about 3 minutes
Securing container images against common vulnerabilities
Prevent container breakouts by scanning images for vulnerabilities, using trusted registries, and removing unnecessary dependencies.
#4about 4 minutes
Hardening pods with security contexts and standards
Enhance pod security by running containers as non-root users, disabling privilege escalation, and enforcing policies with Pod Security Standards.
#5about 3 minutes
Implementing the principle of least privilege with RBAC
Use Role-Based Access Control (RBAC) to grant users and service accounts only the specific permissions they need at the namespace level.
#6about 2 minutes
Isolating pod-to-pod traffic with network policies
Restrict communication between pods by default and define explicit allow rules using network policies and CNI plugins like Calico.
#7about 2 minutes
Protecting the critical ETCD datastore from unauthorized access
Secure the cluster's central datastore, etcd, by enforcing TLS communication with the API server and using a separate certificate authority.
#8about 1 minute
Automating policy enforcement with admission controllers
Use tools like Kyverno, Kubewarden, or OPA Gatekeeper as admission controllers to automatically validate and enforce security policies at scale.
#9about 2 minutes
Key takeaways for hardening Kubernetes clusters
A summary of essential practices includes hardening images, using RBAC, isolating traffic, protecting etcd, and automating policy enforcement.
Related jobs
Jobs that call for the skills explored in this talk.
IGEL Technology GmbH
Bremen, Germany
Senior
Java
IT Security
VECTOR Informatik
Stuttgart, Germany
Senior
Kubernetes
Terraform
+1
zeb consulting
Frankfurt am Main, Germany
Remote
Junior
Intermediate
Senior
Amazon Web Services (AWS)
Cloud Architecture
+1
Matching moments
06:25 MIN
Security best practices for containers and Kubernetes
Microservices: how to get started with Spring Boot and Kubernetes
02:52 MIN
Q&A on managed Kubernetes security in the cloud
Kubernetes Security - Challenge and Opportunity
04:28 MIN
Identifying common Kubernetes security vulnerabilities
Kubernetes Security - Challenge and Opportunity
02:04 MIN
Centralizing security services in a Kubernetes ecosystem
DevSecOps: Security in DevOps
08:13 MIN
Understanding the Kubernetes threat landscape and adversaries
Hacking Kubernetes: Live Demo Marathon

03:37 MIN
Addressing unique data protection challenges in Kubernetes
It's all about the Data
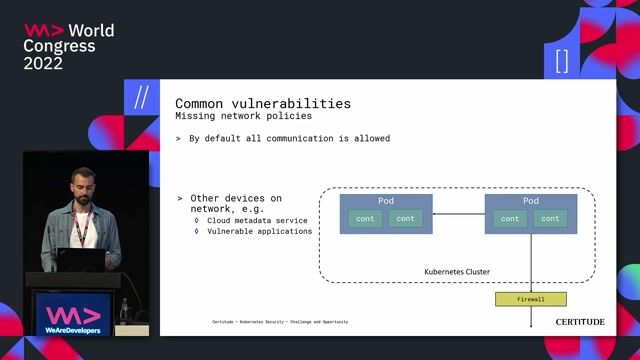
04:04 MIN
Addressing networking and multi-tenancy security challenges
Kubernetes Security - Challenge and Opportunity
07:59 MIN
Securing containers and infrastructure as code (IAC)
Maturity assessment for technicians or how I learned to love OWASP SAMM
Featured Partners
Related Videos
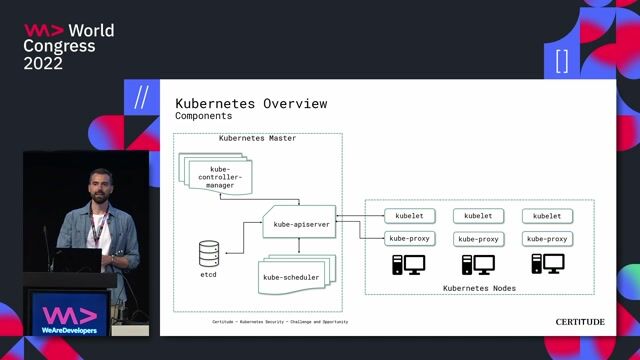 42:45
42:45Kubernetes Security - Challenge and Opportunity
Marc Nimmerrichter
 46:36
46:36Hacking Kubernetes: Live Demo Marathon
Andrew Martin
 44:00
44:00Enhancing Workload Security in Kubernetes
Dimitrij Klesev & Andreas Zeissner
 28:47
28:47Turning Container security up to 11 with Capabilities
Mathias Tausig
 27:52
27:52Chaos in Containers - Unleashing Resilience
Maish Saidel-Keesing
 24:47
24:47Supply Chain Security and the Real World: Lessons From Incidents
Adrian Mouat
 57:24
57:24Mastering Kubernetes – Beginner Edition
Hannes Norbert Göring
 29:50
29:50Real-World Security for Busy Developers
Kevin Lewis
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.

SVA System Vertrieb Alexander GmbH
Azure
Openshift
Kubernetes
Google Cloud Platform
Amazon Web Services (AWS)



virtual7 GmbH
Köln, Germany
Senior
DevOps
Docker
Openshift
Kubernetes
Agile Methodologies
+1


virtual7 GmbH
Mainz, Germany
Senior
DevOps
Docker
Openshift
Kubernetes
Agile Methodologies
+1

virtual7 GmbH
Düsseldorf, Germany
Senior
DevOps
Docker
Openshift
Kubernetes
Agile Methodologies
+1


virtual7 GmbH
Bonn, Germany
Senior
DevOps
Docker
Openshift
Kubernetes
Agile Methodologies
+1