Christoph Eicke
IP Authentication: A Tale of Performance Pitfalls and Challenges in Prod
#1about 1 minute
The case against IP-based authentication for microservices
Migrating a PHP monolith to microservices revealed the fundamental problems with using IP-based authentication, a method you should avoid.
#2about 6 minutes
Understanding the mechanics and tradeoffs of IP authentication
IP authentication simplifies user access for large institutions by mapping an IP address to a user, but it creates issues with user tracking, licensing, and technical complexity.
#3about 3 minutes
Investigating initial deployment failures and performance issues
The first two production deployments failed due to massive error spikes, leading to an architectural change from a slow MySQL database lookup to a faster Redis cache.
#4about 2 minutes
Adopting a fail forward strategy to debug in production
After repeated failures, the team decided to stop rolling back and instead collaborated directly with customers in screen-sharing sessions to diagnose the issue live.
#5about 2 minutes
Discovering the root cause of the infinite redirect loop
The core problem was that legacy and new AWS accounts read the user's IP from different headers, causing a mismatch that sent cookieless bots into an infinite redirect loop.
#6about 2 minutes
How proxies and data entry errors break assumptions
The investigation revealed that academic and corporate proxies often rewrite URLs and strip cookies, and a simple data entry error in the CRM granted access to 1.5% of the internet.
#7about 1 minute
Lessons in collaborative problem-solving and architecture evolution
Using mob programming sessions during the crisis strengthened the team, and the final architecture evolved from Lambda to Fargate for cost and performance reasons.
Related jobs
Jobs that call for the skills explored in this talk.
IGEL Technology GmbH
Bremen, Germany
Senior
Java
IT Security
Wilken GmbH
Ulm, Germany
Senior
Amazon Web Services (AWS)
Kubernetes
+1
Matching moments
13:04 MIN
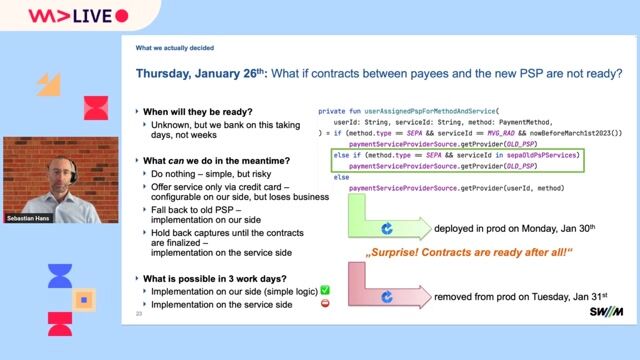
Managing the live migration and resolving production issues
Migrating half a million users to a new payment service provider
03:25 MIN
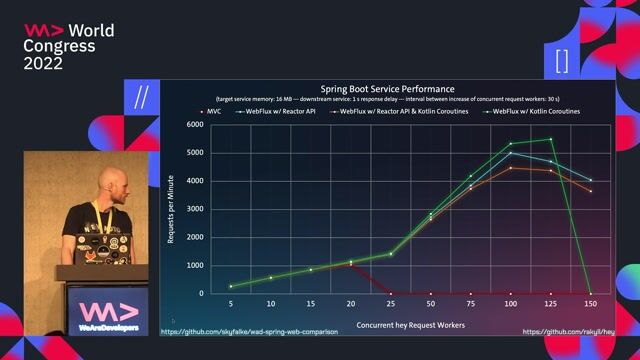
Identifying the limitations of the initial Cloud Foundry platform
Back(end) to the Future: Embracing the continuous Evolution of Infrastructure and Code
18:44 MIN
Answering audience questions on authorization best practices
Un-complicate authorization maintenance
03:20 MIN
Lessons from handling massive, unexpected traffic spikes
API‑First: How Twilio Designs for Developers - Justin Kitagawa (Twilio)

01:53 MIN
Reflecting on early design choices and the problem with DNS
Opening Keynote by Sir Tim Berners-Lee

13:02 MIN
Q&A on Replay.io architecture, adoption, and CI/CD
Fighting test flakiness with time machines

06:21 MIN
A personal story of breaking production at scale
I broke the production
02:46 MIN
Understanding critical architectural trade-offs and anti-patterns
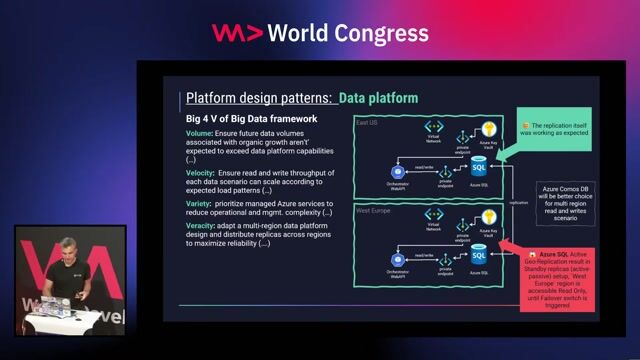
Azure-Well Architected Framework - designing mission critical workloads in practice
Featured Partners
Related Videos
 49:52
49:52Accelerating Authentication Architecture: Taking Passwordless to the Next Level
Yedidya Schwartz
 50:06
50:06Single Server, Global Reach: Running a Worldwide Marketplace on Bare Metal in a Cloud-Dominated World
Jens Happe
 28:12
28:12Scaling: from 0 to 20 million users
Josip Stuhli
 27:55
27:55Going Beyond Passwords: The Future of User Authentication
Gift Egwuenu
 29:38
29:38Answering the Million Dollar Question: Why did I Break Production?
Luís Ventura
 22:24
22:24Reliable scalability: How Amazon.com scales on AWS
Florian Mair
 45:19
45:19Security Challenges of Breaking A Monolith
Reinhard Kugler
 30:48
30:48The AI Agent Path to Prod: Building for Reliability
Max Tkacz
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.

glueckkanja AG
Azure
Powershell
Microsoft Access
Microsoft Active Directory
Scripting (Bash/Python/Go/Ruby)

Devoteam
Frankfurt am Main, Germany
Remote
API
.NET
Microsoft Office
Microsoft Active Directory

ITech Consult AG
Bern, Switzerland
CHF101-185K
UML
Software Architecture
Continuous Integration
Amazon Web Services (AWS)

Cisco Systems GmbH
Eschborn, Germany
Intermediate
Microservices
Cisco networks

CoreWeave Europe
Charing Cross, United Kingdom
Remote
£98-130K
Senior
Kubernetes
Scripting (Bash/Python/Go/Ruby)

Webseite Komm.ONE
Heilbronn, Germany
Remote



Webseite EY Deutschland
Hannover, Germany