Oliver Seitz
Docker exec without Docker
#1about 1 minute
Understanding how the docker exec command really works
The talk explores what happens under the hood when you run `docker exec` and demonstrates how to achieve the same result without using Docker.
#2about 1 minute
Deconstructing the Docker stack to its Linux primitives
Docker is built on top of lower-level components like containerD and runC, which ultimately rely on core Linux kernel features like Cgroups and namespaces.
#3about 3 minutes
Limiting container resources using Linux Cgroups
Cgroups are a Linux kernel feature used to limit and account for resource usage, such as CPU, memory, process IDs, and I/O for a collection of processes.
#4about 4 minutes
A live demo of limiting process CPU with Cgroups
A practical demonstration shows how to create a new Cgroup, define a CPU usage limit in the `cpu.max` file, and assign a running process to it.
#5about 6 minutes
Isolating processes from each other using Linux namespaces
Namespaces provide process isolation by virtualizing system resources like network interfaces, mount points, process IDs, and user IDs for each container.
#6about 9 minutes
Replicating `docker exec` with the `nsenter` command
By finding a container's process ID on the host, you can use the `nsenter` command to enter all of its namespaces and gain a shell inside the container without using Docker.
#7about 3 minutes
Key takeaways and advice for deeper technical understanding
A summary of how Cgroups and namespaces power containers is followed by advice for developers to dig deeper into technologies, focus on one topic at a time, and share their knowledge.
Related jobs
Jobs that call for the skills explored in this talk.
Power Plus Communications
Mannheim, Germany
Intermediate
Senior
Docker
Kubernetes
+1
VECTOR Informatik
Stuttgart, Germany
Senior
Kubernetes
Terraform
+1
Wilken GmbH
Ulm, Germany
Senior
Amazon Web Services (AWS)
Kubernetes
+1
Matching moments
07:05 MIN
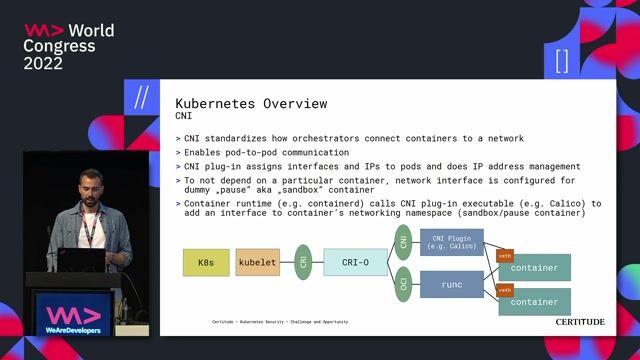
How container isolation works in the Linux kernel
Kubernetes Security - Challenge and Opportunity
07:06 MIN
Understanding Docker fundamentals for application deployment
Rust and Docker: Let's build an AI-powered app!

01:59 MIN
Understanding container isolation with namespaces and cgroups
Docker network without Docker
07:11 MIN
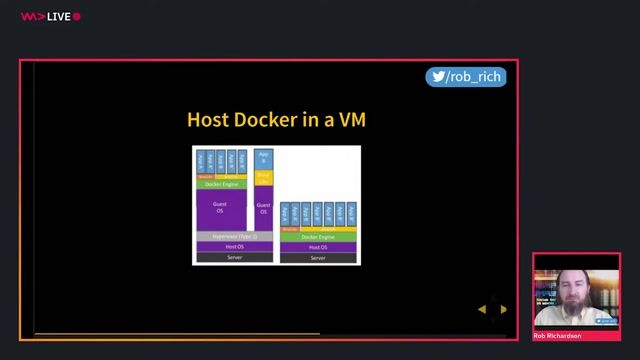
Exploring the Docker ecosystem and image layers
Database DevOps with Containers

02:31 MIN
Introducing bootable containers and the CNCF donation
Bootable AI Containers with Podman Desktop
02:20 MIN
Why the creator of Docker is interested in WebAssembly
WebAssembly: The Next Frontier of Cloud Computing
01:35 MIN
Why Dockerfile security is a critical foundation
A practical guide to writing secure Dockerfiles
02:35 MIN
Using containers to improve security and deployment
DevSecOps: Security in DevOps
Featured Partners
Related Videos
 28:26
28:26Docker network without Docker
Oliver Seitz
 28:47
28:47Turning Container security up to 11 with Capabilities
Mathias Tausig
 50:09
50:09Compose the Future: Building Agentic Applications, Made Simple with Docker
Mark Cavage, Tushar Jain, Jim Clark & Yunong Xiao
 42:45
42:45Kubernetes Security - Challenge and Opportunity
Marc Nimmerrichter
 27:55
27:55This Is Not Your Father's .NET
Don Schenck
 29:19
29:19Bootable AI Containers with Podman Desktop
Kevin Dubois & Cedric Clyburn
 28:30
28:30All things Docker Compose!
Michael Irwin
 32:19
32:19Containers and Kubernetes made easy: Deep dive into Podman Desktop and new AI capabilities
Stevan Le Meur
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.



Softwarezentrum Böblingen/Sindelfingen e.V.
Böblingen, Germany
Remote
Intermediate
GIT
Bash
Azure
Linux
+5

Rheinmetall
Berlin, Germany
Senior
Azure
Linux
Puppet
Ansible
Openshift
+4

Silkhom
Canton of Cholet-1, France
€40-50K
Senior
DNS
Linux
DevOps
Routing

Dataport
Hamburg, Germany
Unix
Linux
Ansible
PostgreSQL
Continuous Integration

Deos Ag
Rheine, Germany
Linux
Python
Ansible
Powershell
Prometheus
+5

Rocken Schweiz/suisse/switzerland
Gelsenkirchen, Germany
Remote
Bash
Linux
Docker
Ansible
+3
